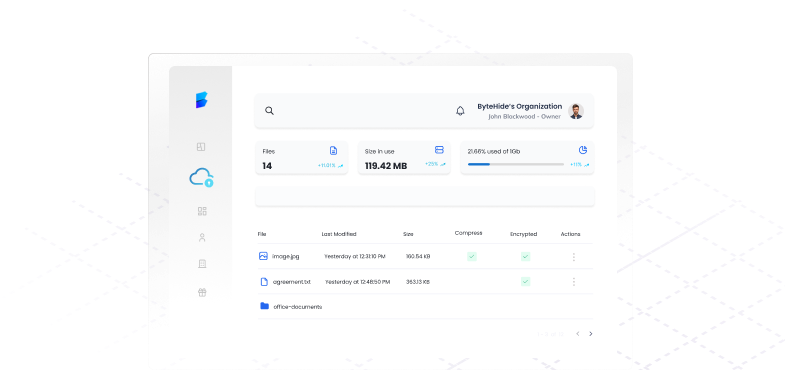
Secure and Accessible Object Storage for your application
Simplify your data storage with our S3 – compatible object storage solution powered by Post-Quantum Cryptographysetting new standards in data protection.
1
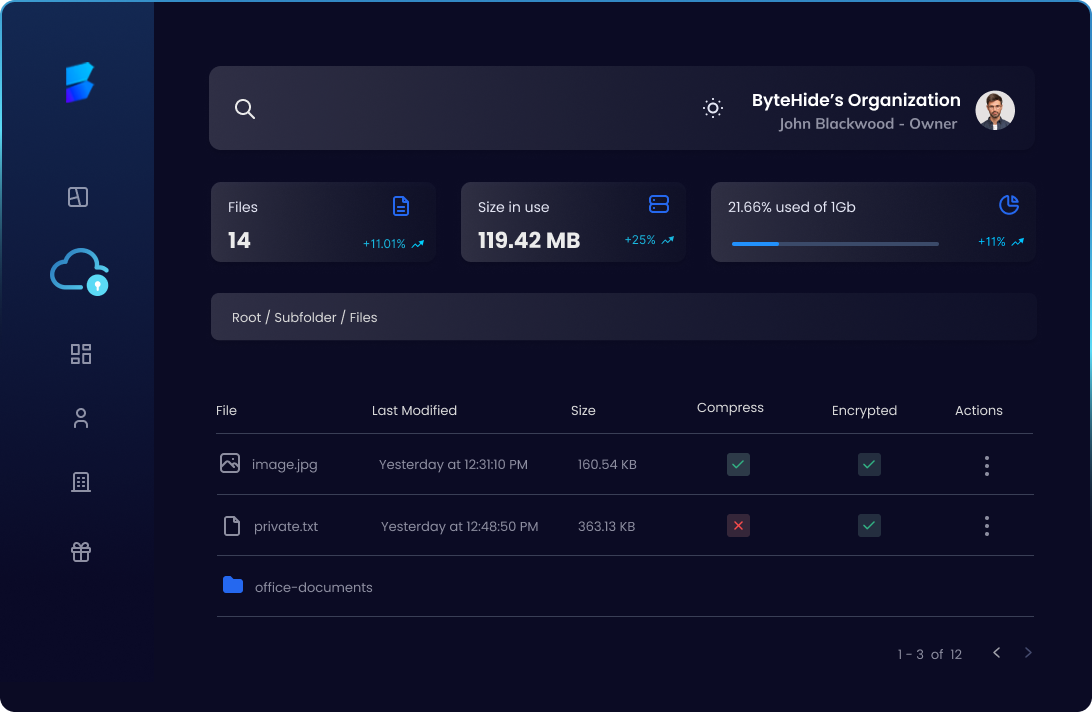
Effortless Integration, Powerful Tools
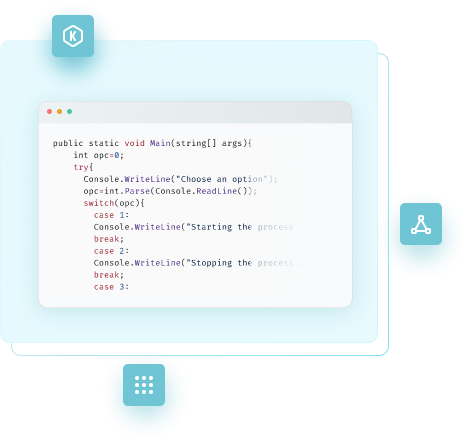
Manage Storage with Just a Few Lines
Start managing your application’s storage efficiently with just a few lines of code. ByteHide Storage makes it easy to set up advanced,
secure storage solutions tailored to developers’ needs, helping you focus on building while we handle the rest.
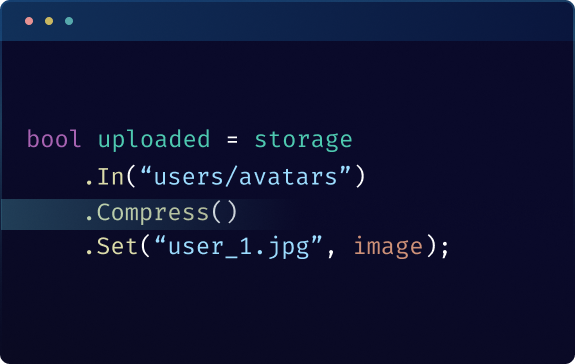
Automatic Compression
Automatically compress files before uploading to save storage space and reduce transfer times, maximizing storage efficiency.
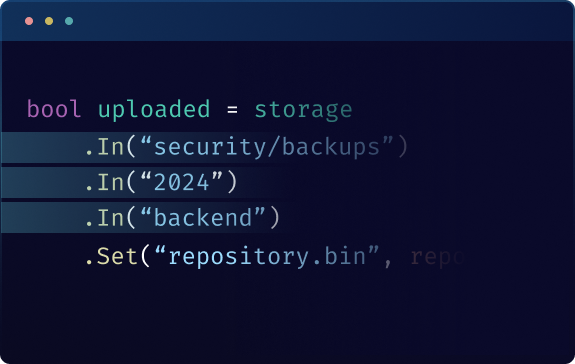
Folder Structuring
Organize your files into custom folders for quick, logical access, making data management and structuring within your application seamless.
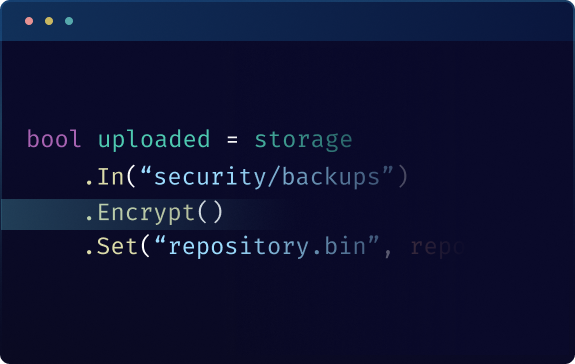
Environment-Based Encryption
Encrypt files directly from the device using advanced methods, with the option to use your own keys for complete privacy.
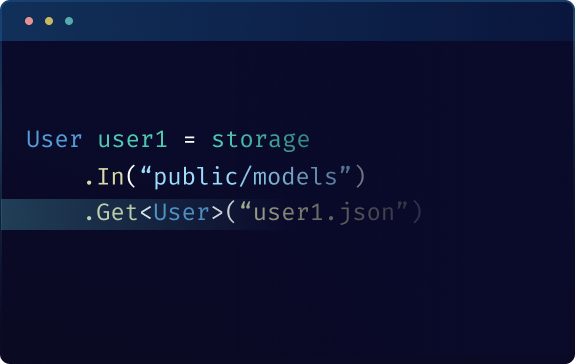
Multiple Structured Formats
Upload and download serialized models, images, binaries, and automatically convert downloads to the correct format.
2
Built-In Privacy, Unbreakable Security
Your Data, Only for Your Eyes
Once your files are uploaded, ByteHide Storage goes above and beyond to safeguard your data. With advanced encryption and privacy controls,
rest assured that your files are secure, private, and accessible only to those you trust.
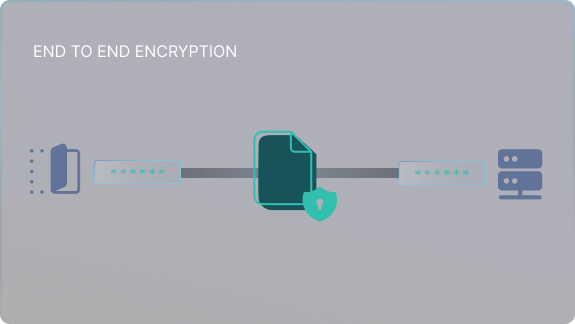
End-to-End Encryption
Ensure your files remain private with end-to-end encryption, where files are encrypted before they leave your application and remain protected in storage, accessible only to you.

Zero-Knowledge Privacy
Your data stays exclusively yours. With zero-knowledge encryption, we have no access to your encryption keys or file contents, guaranteeing absolute privacy.
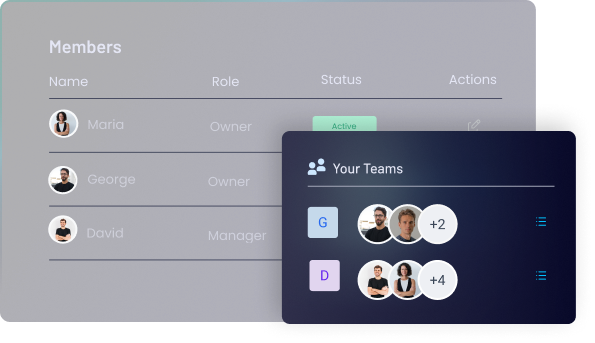
Access Control Management
Customize access permissions for each file, choosing between public, restricted, or temporary access, to ensure data is only available to the right users.

File Integrity Verification
Automatically validate the integrity of your files to ensure they haven’t been tampered with, adding a robust layer of security.
3
Quantum Resilience for Tomorrow’s Security
Post-Quantum Encryption
Protect your data against quantum computing threats with next-generation cryptographic algorithms designed to secure your information in an evolving digital landscape. Our post-quantum encryption ensures your files remain protected even in the face of advanced computational challenges, making your security future-proof.
Kyber Family
Kyber512
Kyber768
Kyber1024
FrodoKEM
FrodoKEM-640-SHAKE
FrodoKEM-976-SHAKE
FrodoKEM-1344-SHAKE
ML-KEM
ML-KEM-512
ML-KEM-768
ML-KEM-1024
Quantum Resistant
Designed to provide robust layers of security, this technology offers exceptional resilience against evolving cyber threats. By combining classical and quantum defenses, it ensures maximum protection against potential attacks.
Production Ready
Built to industry-standard specifications, this solution integrates seamlessly into existing infrastructures. It is optimized to offer superior performance, scalability and ease of deployment, ensuring that your system is always ready to be deployed.
Future Proof
Adaptable to advances in quantum computing technology, this technology is regularly updated to ensure continuous security. Based on visionary cryptographic principles, it is built to meet the challenges of the future.
The Future of Data Security
Quantum Threat Landscape
Traditional encryption becoming vulnerable
to quantum attacks
Critical infrastructure at risk from quantum
computing advances
Post-Quantum Solution
Quantum-resistant algorithms protecting
against future threats
Long-term security for sensitive data
and communications
As technology advances, so do the
threats to our data security. Implementing
post-quantum cryptographic solutions ensures
your information remains secure
against both current and future threats.
Book a Free DemoAs technology advances, so do the
threats to our data security. Implementing
post-quantum cryptographic solutions ensures
your information remains secure
against both current and future threats.
COMPARISON WITH OTHER STORAGE SOLUTIONS
Why ByteHide Storage Stands Out
Traditional Solutions
Easy Integration
Complex and time-consuming
End-to-End Encryption
Not natively available
Zero-Knowledge
Not implemented
Privacy and Access Control
Depends on configurations, added complexity
Transparent Costs
Complex pricing structure, high costs
Advanced Features
Limited or additional
Ease of Use
Requires advanced experience
Easy Integration
Fast and easy
End-to-End Encryption
Integrated by default
Zero-Knowledge
By design, it’s zero-knowledge
Privacy and Access Control
By default, flexible and configurable
Transparent Costs
Clear and competitive, compression before storing
Advanced Features
Natively integrated
Ease of Use
Focused on simplicity, developer-first
Traditional Solutions
Easy Integration
Complex and time-consuming
End-to-End Encryption
Not natively available
Zero-Knowledge
Not implemented
Privacy and Access Control
Depends on configurations, added complexity
Transparent Costs
Complex pricing structure, high costs
Advanced Features
Limited or additional
Ease of Use
Requires advanced experience
Easy Integration
Fast and easy
End-to-End Encryption
Integrated by default
Zero-Knowledge
By design, it’s zero-knowledge
Privacy and Access Control
By default, flexible and configurable
Transparent Costs
Clear and competitive, compression before storing
Advanced Features
Natively integrated
Ease of Use
Focused on simplicity, developer-first
Getting started with Storage
is simple
.NET
.NET installation
dotnet add package Bytehide.Storage --version latest.NET Code
// Startup:
var storage = new StorageManager("");
// Upload a file:
bool uploaded = storage.Set("main/images/photo.jpg", image);
// Download a file:
var file = storage.Get("main/images/photo.jpg");
Getting started with Storage
is simple
.NET
.NET installation
dotnet add package Bytehide.Storage --version latest.NET Code
// Startup:
var storage = new StorageManager("");
// Upload a file:
bool uploaded = storage.Set("main/images/photo.jpg", image);
// Download a file:
var file = storage.Get("main/images/photo.jpg");
Frequently asked questions
What is Storage and how does it enhance data management for applications?
Storage is an Object Storage solution designed for the efficient management of application data. It ensures data integrity while providing seamless management of files and databases, allowing businesses to scale without worrying about data logistics.
How does Storage ensure the security of my application data?
Storage employs robust security measures, including end-to-end encryption and a zero-knowledge model, to safeguard your application data from unauthorized access. This ensures that your data remains protected from the moment it is uploaded until it is downloaded.
What are the benefits of using Storage's easy integration features?
With an intuitive SDK, Storage allows developers to quickly integrate secure data storage into their applications. This enables immediate access to advanced storage solutions without extensive setup, so you can focus more on developing core application features.
What makes Storage's pricing structure advantageous for businesses?
Storage offers a transparent and competitive pricing model that is designed to optimize costs while maintaining high-quality and secure storage solutions. This allows businesses to efficiently manage resources without compromising on performance or security.
How do Storage's customizable features support different project needs?
Storage provides a range of advanced features that are customizable to fit the unique requirements of any project. Whether you need specialized access controls or tailored backup solutions, Storage adapts to support your specific business objectives.
What steps does Storage take to ensure data compatibility and support?
Storage is engineered for maximum compatibility with a wide array of technologies and platforms. Our dedicated support team is always available to assist, ensuring smooth integration and operation with the tools you already use.
How does Storage compare to other object storage solutions in terms of scalability?
Storage is designed to seamlessly scale alongside your business. Whether you’re handling increasing data loads or expanding your user base, Storage provides the infrastructure to grow without the common pitfalls associated with scaling storage solutions.
What makes Storage a reliable choice for businesses seeking secure data solutions?
Storage combines robust encryption, easy integration, and a user-friendly interface, making it an ideal choice for businesses looking to secure their data while maintaining ease of access and management. Its innovative features ensure your data is both protected and readily available for business operations.

