Protect your legal software and legal data that it processes, from digital contracts to critical business logic, without the hassle for your development team.




Why do LegalTech companies need App Security?
Digital legal platforms operate under constant pressure to ensure the privacy, integrity, and traceability of the sensitive information they handle. From confidential documents to proprietary legal logic, any breach or unauthorized access can have serious regulatory and reputational consequences. Reverse engineering, data leaks, and lack of visibility into how applications behave after deployment expose legal tech companies to significant risk. In a sector built on trust and compliance, robust application security isn’t just a best practice it’s something your clients and partners will expect you to prove.
ByteHide’s Solution
ByteHide unifies your software security within a single platform.
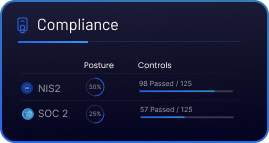
Compliance
Keep Your LegalTech Compliance On Track
ByteHide helps LegalTech companies meet key compliance standards like ISO/IEC 27001, SOC 2, and GDPR by embedding robust security across the entire software lifecycle. From development to production, we ensure your legal data, proprietary logic, and user access are protected and auditable.
ISO/IEC 27001 – Information Security Management
ISO 27001 defines best practices for managing sensitive information securely. ByteHide supports this standard by enforcing secure coding practices, protecting legal data in transit and at rest, and maintaining visibility into how applications behave after deployment.
SOC 2 – Trust Service Criteria for Digital Services
SOC 2 evaluates your ability to safeguard client data based on principles like confidentiality, integrity, and availability. ByteHide strengthens your SOC 2 posture with encrypted activity logs, runtime behavior monitoring, and controls that reduce the risk of unauthorized access or data leakage.
GDPR – General Data Protection Regulation
GDPR requires strong measures to protect personal and sensitive data, including legal and judicial information. ByteHide enables compliance through secret management, access control, and real-time protection against reverse engineering or unauthorized manipulation of legal logic.
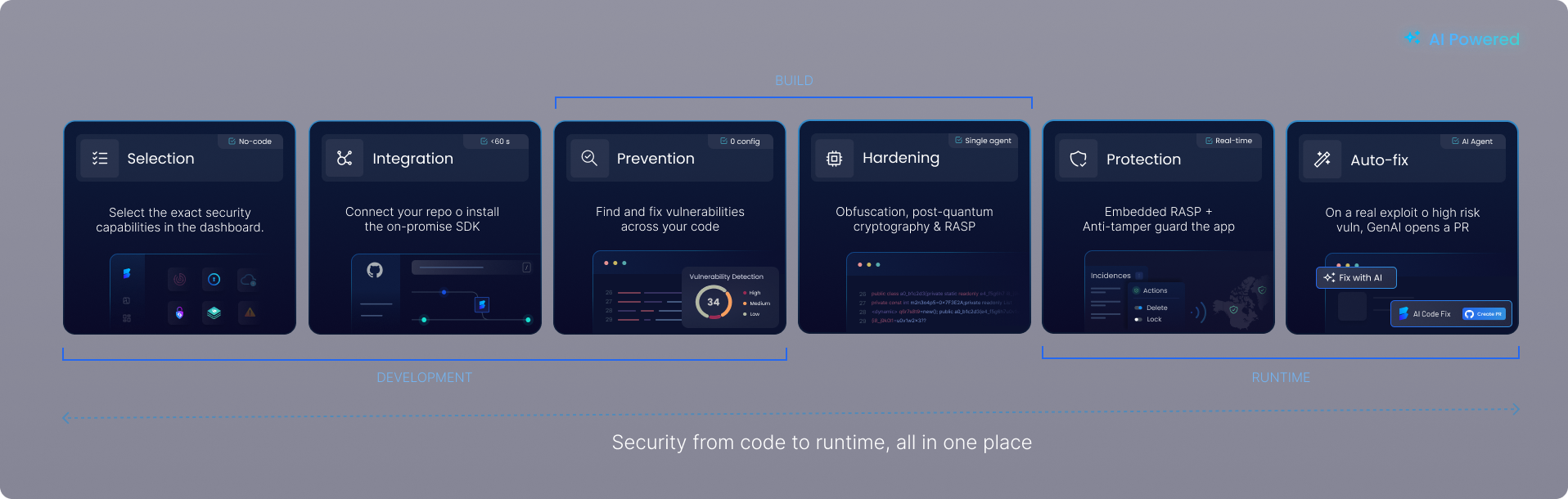
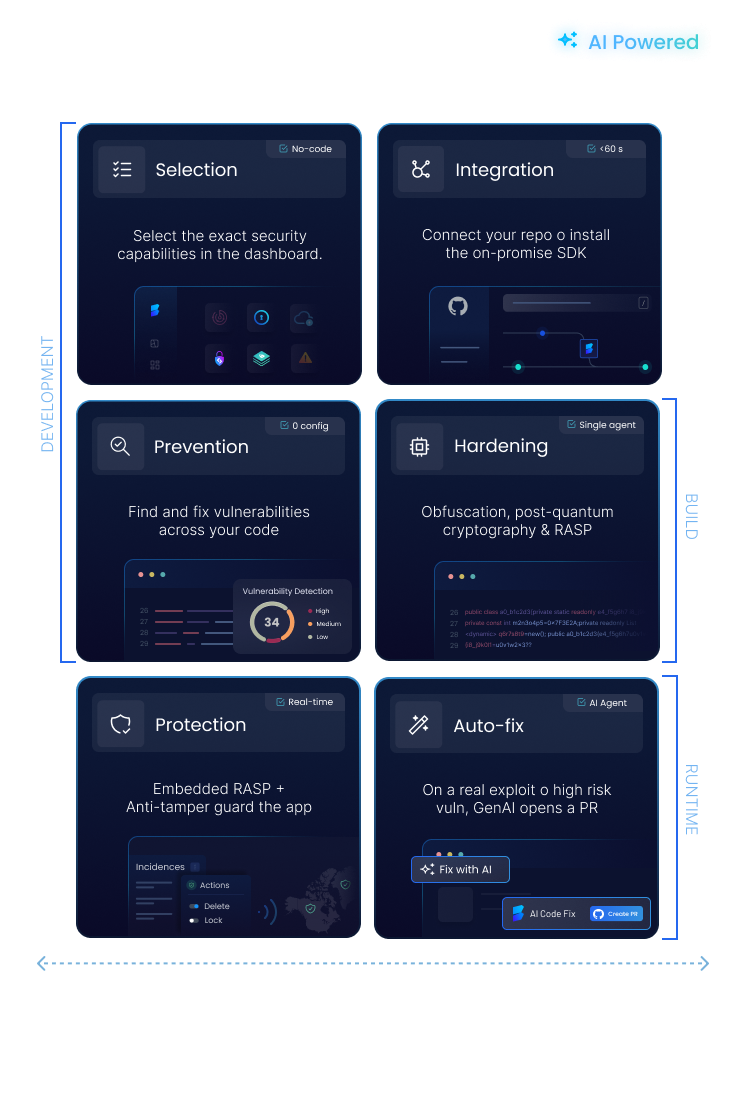
Next-Gen Security Features
AI Static Code Analysis
Scans your source code for critical security vulnerabilities like SQL injection, XSS, and buffer overflows. AI-powered analysis reduces false positives by 85% and offers AI-driven autofix to remediate issues autonomously. Works out-of-the-box and supports all major languages.

Software Composition Analysis (SCA)
Analyzes third-party components (libraries, frameworks, dependencies) for vulnerabilities. Identifies and manages known CVEs, reducing supply chain risks.
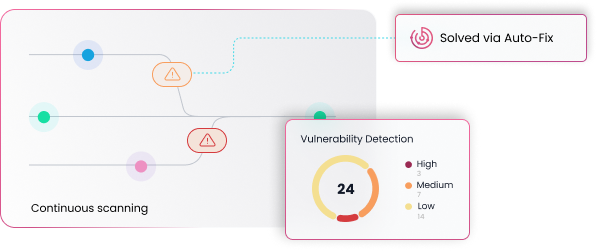
Secrets Detection
Scans your codebase, configurations, and repositories to detect hardcoded credentials, API keys, and sensitive information. Identifies and remediates exposed secrets before they become a threat.
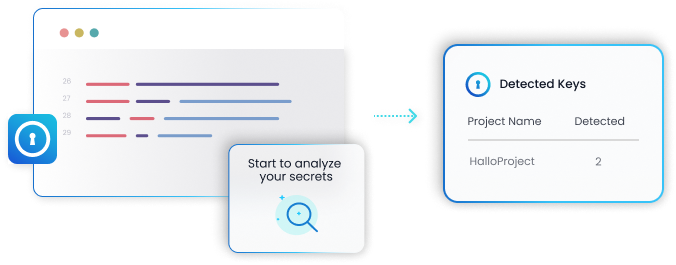
Secure Secrets Management
Provides a centralized, encrypted vault for storing and distributing API keys, database passwords, and other sensitive credentials. Reduces your attack surface and improves security posture.
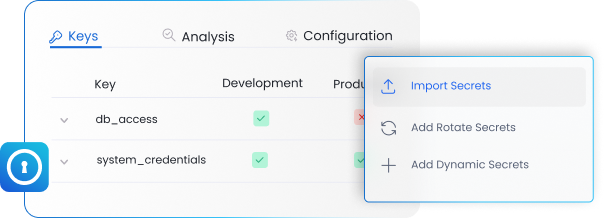
Code Security & Obfuscation
Safeguard your proprietary code and intellectual property from reverse engineering and tampering. Advanced code obfuscation techniques transform your application’s logic, making it extremely difficult for attackers to understand and exploit, while maintaining full functionality.
Runtime Protection & Monitoring (RASP)
Actively monitors and defends your applications against attacks at runtime. Immediately detects and blocks exploits like zero-day threats, injections, tampering, OWASP top 10 and unauthorized access. Ensures continuous application integrity without requiring code changes.

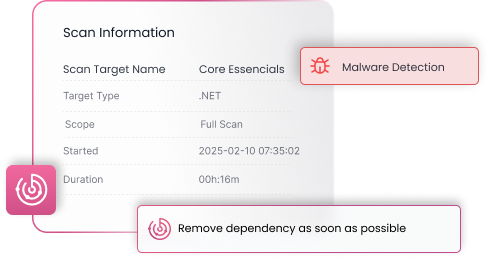
Malware Detection
Protects your software supply chain by detecting malware in dependencies, injected code, and third-party libraries. Proactively scans files and data your application manipulates, including those in storage, to ensure comprehensive protection against malicious threats and maintain system integrity.
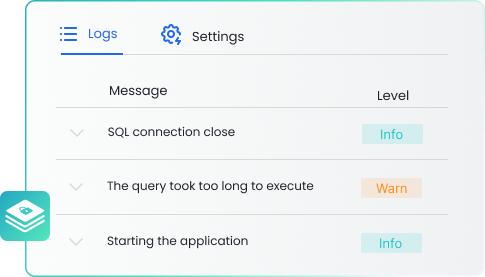
Secure Log Management
Centralizes, encrypts, and manages all your application and system logs. Ensures data integrity, provides irrefutable audit trails, and enables rapid incident response while protecting sensitive information.
Post-Quantum Secure Storage
Protects sensitive data against future cryptographic threats. Offers highly secure data storage leveraging advanced post-quantum encryption algorithms, ensuring confidentiality and integrity even against quantum computing attacks.

Application Security Posture Management (ASPM)
Gain a holistic view of your application security risks across the entire SDLC. ByteHide centralizes security findings from all modules (SAST, SCA, Secrets, Runtime) and contextualizes them to help you prioritize critical vulnerabilities, track remediation progress, and ensure continuous compliance.

Unboring LegalTech AppSec for High-Growth Teams
Say goodbye to corporate security headaches. Bytehide streamlines LegalTech application security, helping you fast-track code and compliance, while saving valuable time and money.
All-in-one
Secure your software from the first line of code to production. Our comprehensive platform integrates all necessary security tools into one seamless solution.
Up to 7x Faster
Dramatically accelerate fixes. Our AI leverages deep context across your entire security chain, eliminating false positives and autonomously fixing issues where other tools generate noise due to lack of insight.
Up to 65% Cost Savings
Achieve enterprise-grade security for significantly less. Reduce tool sprawl and operational overhead, cutting your AppSec budget while maintaining top-tier protection.
Frequently asked questions
Why is application security and data privacy critical for my LegalTech company?
In LegalTech, you handle confidential legal documentation, judicial processes, and contracts, demanding constant privacy, integrity, and traceability. ByteHide offers comprehensive protection to shield your business logic and sensitive data flows, reinforcing the privacy and integrity of your legal information from code to production, without complicating your development team.
How does ByteHide help my LegalTech company comply with ISO 27001, SOC 2, and GDPR?
For your LegalTech, ByteHide facilitates essential regulatory compliance by embedding robust security throughout the entire legal software lifecycle. We help you comply with ISO/IEC 27001, SOC 2, and GDPR by ensuring your legal data, proprietary logic, and user access are protected and auditable.
How can ByteHide prevent legal data leaks before they occur, directly from the code?
ByteHide allows you to detect and mitigate vulnerabilities in your code and third-party libraries that could expose sensitive legal information. Our Radar product scans your software for flaws (like SQL injections or XSS) and detects leaks before deployment. It’s crucial for your privacy that the analysis is performed locally within your environment, without your code or sensitive data being uploaded to our servers.
How does Secrets (Secrets Detection & Management) guarantee the confidentiality of sensitive legal information?
Your LegalTech can secure the “keys” to access your most sensitive data. Our Secrets product detects critical credentials (like API keys or access tokens) directly in your code, which are gateways to sensitive data such as contracts or judicial databases. By securely managing and encrypting these secrets, it prevents their exposure and unauthorized access to confidential legal information.
How does Shield (Code and Business Logic Protection) contribute to the integrity and privacy of business rules in LegalTech?
ByteHide shields your custom legal logic and essential business rules. Our Shield product protects your software’s code and proprietary legal logic to prevent extraction or alteration in production environments. This is crucial for maintaining the integrity of your automated contracts and business rules, and protecting your legal intellectual property.
How does Monitor (Continuous Runtime Monitoring - RASP) provide protection and data traceability for LegalTech applications?
For your LegalTech, ByteHide ensures constant and active vigilance of your applications. Our Monitor product performs continuous monitoring at runtime to detect suspicious access, data leaks, or anomalous behavior. This is essential for applications managing legal documentation, as it prevents leaks or tampering on connected devices and ensures the privacy of legal information in use.
What privacy and security features does Storage (Secure Storage) offer for confidential legal documentation?
ByteHide ensures maximum confidentiality for your legal documentation and contracts. Our Storage product offers end-to-end encryption and a “Zero-Knowledge” model. Your data is encrypted at its source, and only you hold the keys to decrypt it, guaranteeing unbreakable privacy.
How does Logs (Encrypted Audit & Full Traceability) ensure legal compliance and the privacy of activity records?
ByteHide provides encrypted and fully auditable activity logs, essential for legal compliance. Our Logs product offers encrypted audit and complete traceability, compatible with the most demanding legal and privacy requirements. Logs are encrypted from your application to our servers, and sensitive data can be masked within them. This ensures that access and activity records are private, secure, and valid for audits.
How can ByteHide simplify security management in my LegalTech and reduce operational risks?
ByteHide provides you with total visibility and simplified regulatory compliance. The platform unifies protection across the entire legal software lifecycle, from development to execution. Our approach reduces the risk of unauthorized access or leaks and allows your technical team to focus on innovation without additional security efforts.
What are the key benefits of implementing ByteHide for LegalTech application security?
By choosing ByteHide, your LegalTech gains specific legal security for distributed legal software, prevention of leaks before they occur, protection of your proprietary logic and legal data, and total visibility with simplified regulatory compliance. Our all-in-one approach allows you to protect your software and the data it processes without complicating your development team.
Impenetrable Legal Confidentiality
Secure your critical contracts and documentation, shield your proprietary legal logic, and ensure impeccable traceability. Protect your firm’s reputation with seamless security.

Impenetrable Legal Confidentiality
Secure your critical contracts and documentation, shield your proprietary legal logic, and ensure impeccable traceability. Protect your firm’s reputation with seamless security.


