What's New?
Features, updates and enhancements to the ByteHide platform
September 19, 2025

After the success of Logs for .NET, it’s time for JavaScript.
Logs quickly became one of the most requested products in the ByteHide platform, with hundreds of .NET developers already relying on it for secure, centralized, and privacy-first log management. Now,…
August 29, 2025
Two-Factor Authentication (2FA) now available
The security of your account is our top priority, which is why we’re introducing one of the most important features so far: Two-Factor Authentication (2FA). Starting today, you can add…
August 8, 2025
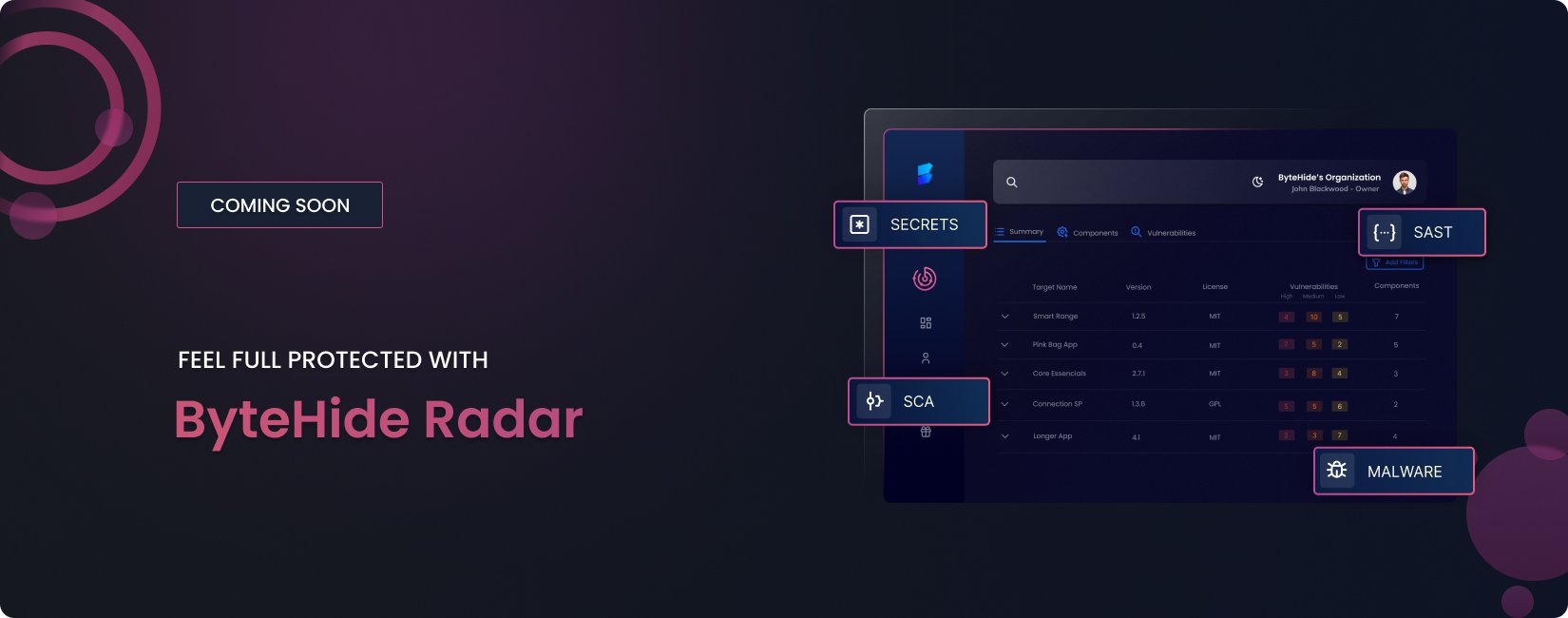
Feel fully protected with Radar.
We’re excited to introduce a new product within the ByteHide platform: Radar, our intelligent and unified security scanner powered by artificial intelligence. Radar is designed to scan your codebase and…
August 1, 2025

New Dashboard: More visibility, more context, more security
We’re excited to introduce the new platform dashboard, a major update that brings a clearer, smarter, and more security-focused experience. We know that managing the security of your projects can…
July 18, 2025

Your logs, now with superpowers
After many requests, because yes, your wishes are our commands, we’ve launched a powerful new console-like experience in ByteHide Logs. Now you can search, filter and export logs instantly with…
July 4, 2025

NextJS for Shield is available now!
The first official module for JavaScript integrations is now available Shield, ByteHide’s most popular obfuscator with over 1 million protected applications, now officially supports Next.js with a native integration module….
June 27, 2025

New in Logs: Collaborative comments with mentions
We’ve just launched a highly requested feature in ByteHide Logs: you can now add comments directly to any log from the control panel and mention teammates to streamline collaboration and…
June 20, 2025

Finally, Shield’s Javascript support is here!
The most popular code obfuscator for .NET is now available for JavaScript Shield, ByteHide’s most popular product, is now available for JavaScript.After protecting over 1 million applications worldwide, we’re taking…
June 6, 2025

Smart Log Analysis and Fix Suggestions AI Powered
New Feature: AI-Powered Log Analysis From now on, when you send a log with context, our AI doesn’t just store it. It analyzes it, understands it, and acts on it:…
May 30, 2025

It’s finally here: choose the storage region in ByteHide Storage
Beyond all the advantages ByteHide Storage already offers such as being one of the first solutions in the world to incorporate real post-quantum encryption, guaranteeing a zero-knowledge architecture where not…
May 23, 2025

New Virtualization Protection
We’re excited to announce a powerful new feature in Shield: Code Virtualization Protection. This protection is designed to completely hide your IL code and method logic from decompilers, making static…
May 16, 2025

Global Configuration & Environment Token Support for Shield
What’s New ByteHide Shield now supports a global configuration file and environment-based project tokens, allowing for centralized control and secure token management. Configuration Options You can now choose between two…
May 9, 2025

Unlock all the exciting new features in Shield 3.0!
Get ready for a massive leap forward with a host of new features, optimizations, and fixes that will elevate your development experience. From cutting-edge Code Virtualization Protection to a redesigned…
May 2, 2025

Introducing Post-Quantum Encryption in ByteHide Storage: A Major Leap in Developer-Focused Cloud Security
With the rise of quantum computing, most traditional encryption methods will eventually become obsolete. That’s why ByteHide Storage is taking a major step forward: we are the first cloud storage…
April 18, 2025

Introducing ByteHide Storage: The Secure, Developer-First Object Storage You’ve Been Waiting For
You asked. You tested. And now it’s official. After months of feedback, testing, and refining with hundreds of early adopters, we’re thrilled to announce the full launch of ByteHide Storage…
April 10, 2025
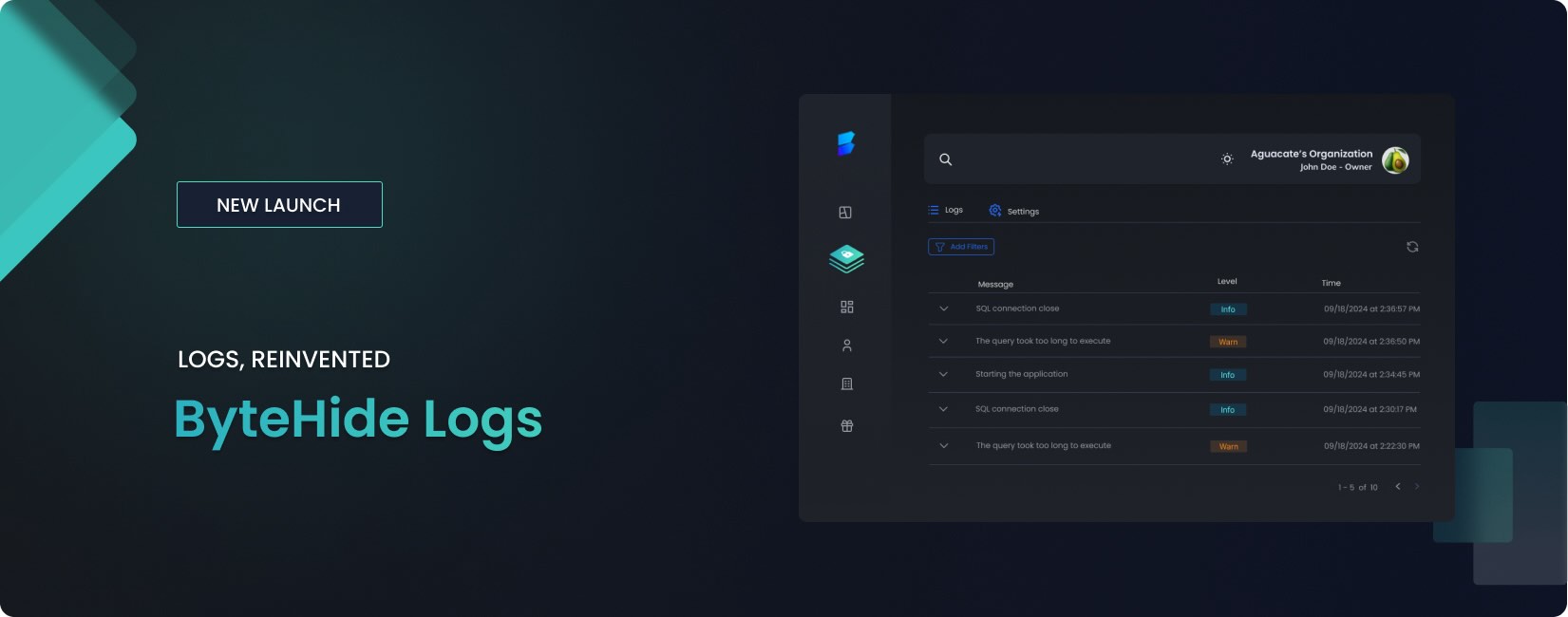
Finally, we’re launching Logs for all of you.
After months of feedback, tests, and hundreds of early users helping us shape the future of secure log management… the wait is over. Over 200 developers have already tested ByteHide…
September 4, 2024

🎓 Welcome to ByteHide University!
Learn how to master our platform, right from your dashboard. At ByteHide, we believe great security starts with clear understanding. That’s why we’re introducing a powerful new feature to take…
August 12, 2024

Linker
ByteHide Linker Integration is a lightweight package designed to merge and compress assemblies of your .NET projects
July 8, 2024

RunTime Application Self-Protection
Monitor is designed to be integrated into client applications as a micro-agent.
June 10, 2024

Secrets Management
Our new Secrets Management feature can help you securely manage all of your sensitive application data, ensuring that it is never exposed.
May 12, 2024

Magic Files for debugging protected applications
Magic files are security files that when placed next to a protected application (in the same directory where they are executed) allow you to execute functions or bypass protections.
February 19, 2024

Local Processing
We are pleased to announce a new feature that makes ByteHide Shield even better, faster and more efficient.
February 7, 2024

New Panel Launched
We migrated to a revamped dashboard, this panel brings with it a number of significant improvements.
November 14, 2023

Secure your Unity Projects
Our intuitive interface and powerful features make safeguarding your Unity projects a breeze.

