In-app protection to stop attacks in real-time
Detect and block threats instantly with real-time protection that stops attacks before they cause harm, so you can focus on growth without constant patching or security worries.
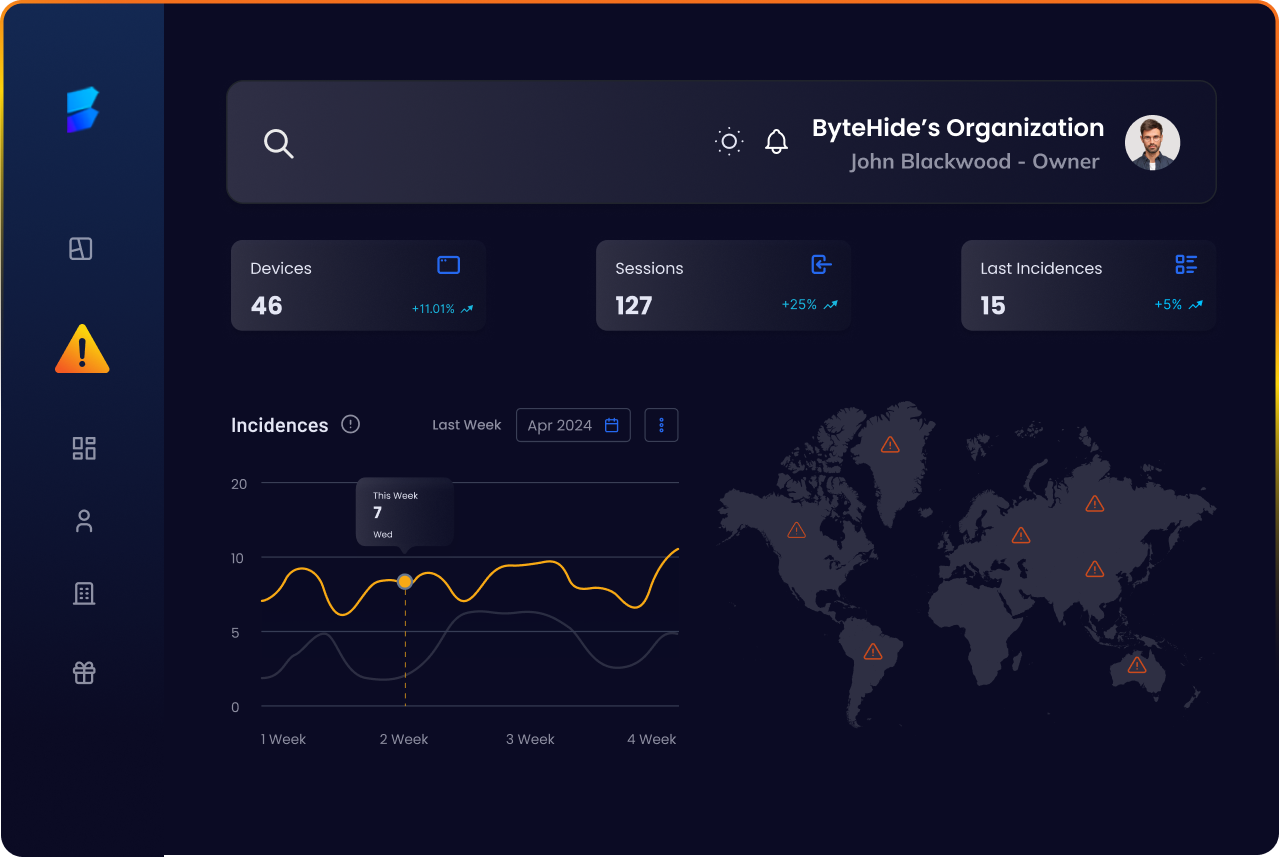
ByteHide Monitor, is able to detect and avert attacks as they occur
Prevent OWASP Mobile Top 10 & Zero Day threats in seconds.

Monitor, is able to detect and avert attacks as they occur
Prevent OWASP Mobile Top 10 & Zero Day threats in seconds.

Superpowers
Give your developers the ability to put security on autopilot and elevate your app’s protection to the next level.
Fully Embedded Security
Unlike perimeter-based solutions like WAFs, Monitor operates from within your application, providing real-time protection embedded at its core.
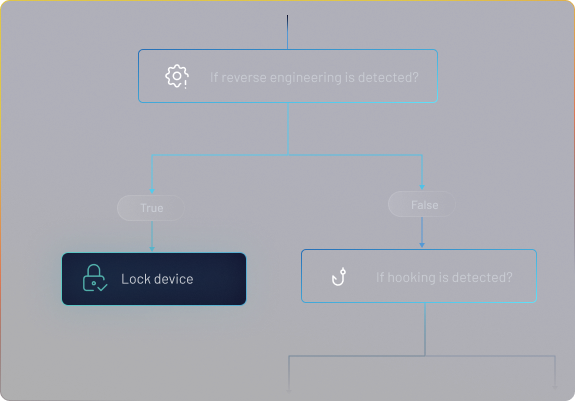
Rules-Based Reactions
Configuration of automatic, customized responses to threats in real-time: from notifications to advanced actions like device-blocking or data deletion, ensuring security without manual intervention.
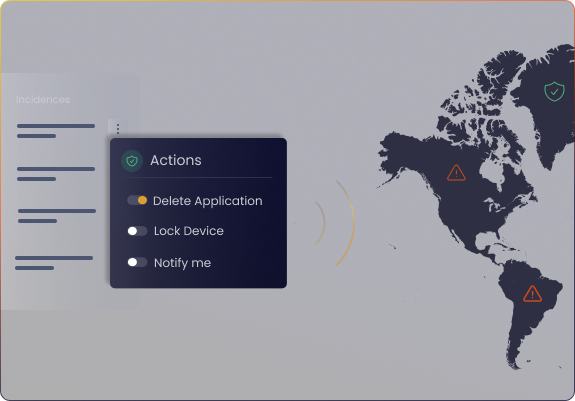
Remote Actions
Full control over security incidents from a central dashboard, allowing you to take immediate actions remotely, such as blocking users, wiping compromised devices, and triggering real-time alerts.
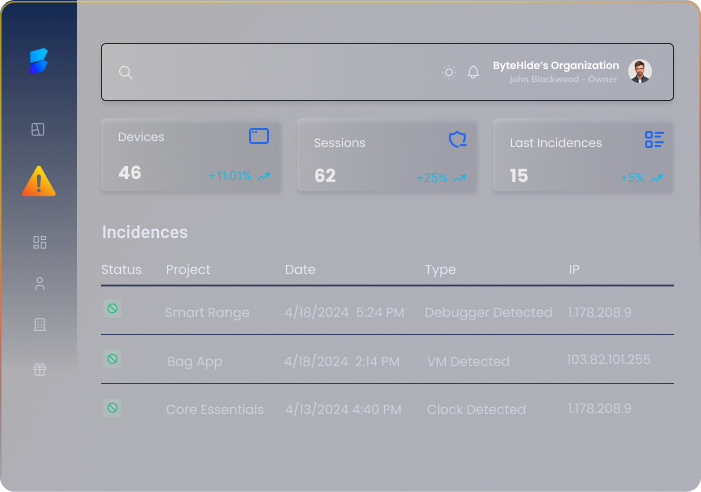
Detailed Threat Logs & Analytics
Track and analyze all security incidents in real-time with detailed logs, helping you understand threats and adapt your defense strategies.

Device & Session Analytics
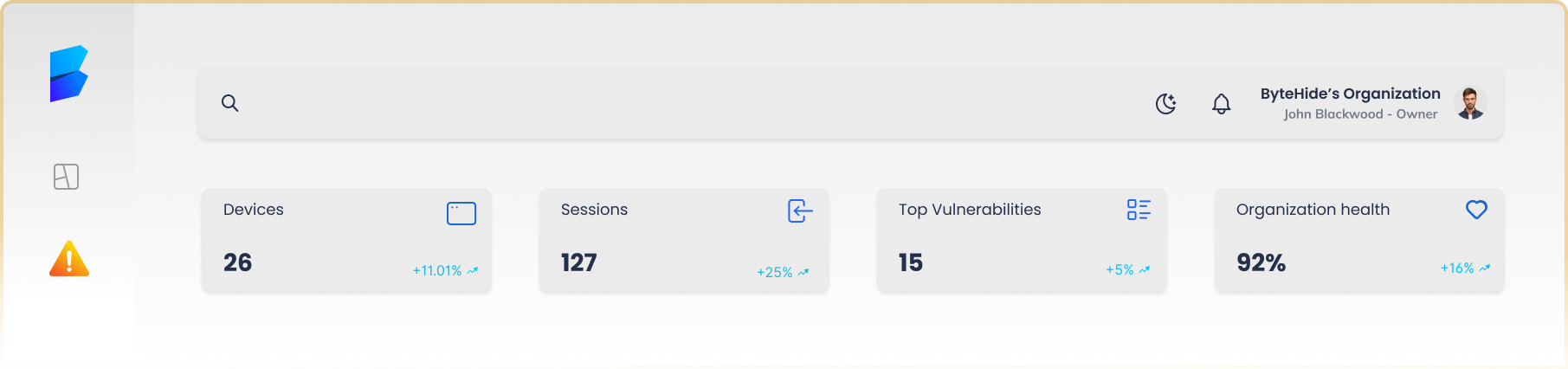
Gain deeper insights into the environment where your app operates with comprehensive device and session analytics. Monitor tracks key device details and user session activities, helping you understand your app’s security landscape.
Monitor, is able to detect and avert attacks as they occur.

Fully Embedded Security
Unlike perimeter-based solutions like WAFs, Monitor operates from within your application, providing real-time protection embedded at its core.

Rules-Based Reactions
Configuration of automatic, customized responses to threats in real-time: from notifications to advanced actions like device-blocking or data deletion, ensuring security without manual intervention.

Remote Actions
Full control over security incidents from a central dashboard, allowing you to take immediate actions remotely, such as blocking users, wiping compromised devices, and triggering real-time alerts

Detailed Threat Logs & Analytics
Track and analyze all security incidents in real-time with detailed logs, helping you understand threats and adapt your defense strategies.

Device & Session Analytics
Gain deeper insights into the environment where your app operates with comprehensive device and session analytics. Monitor tracks key device details and user session activities, helping you understand your app’s security landscape.
How it works
Control your application’s attacks in 3 simple steps
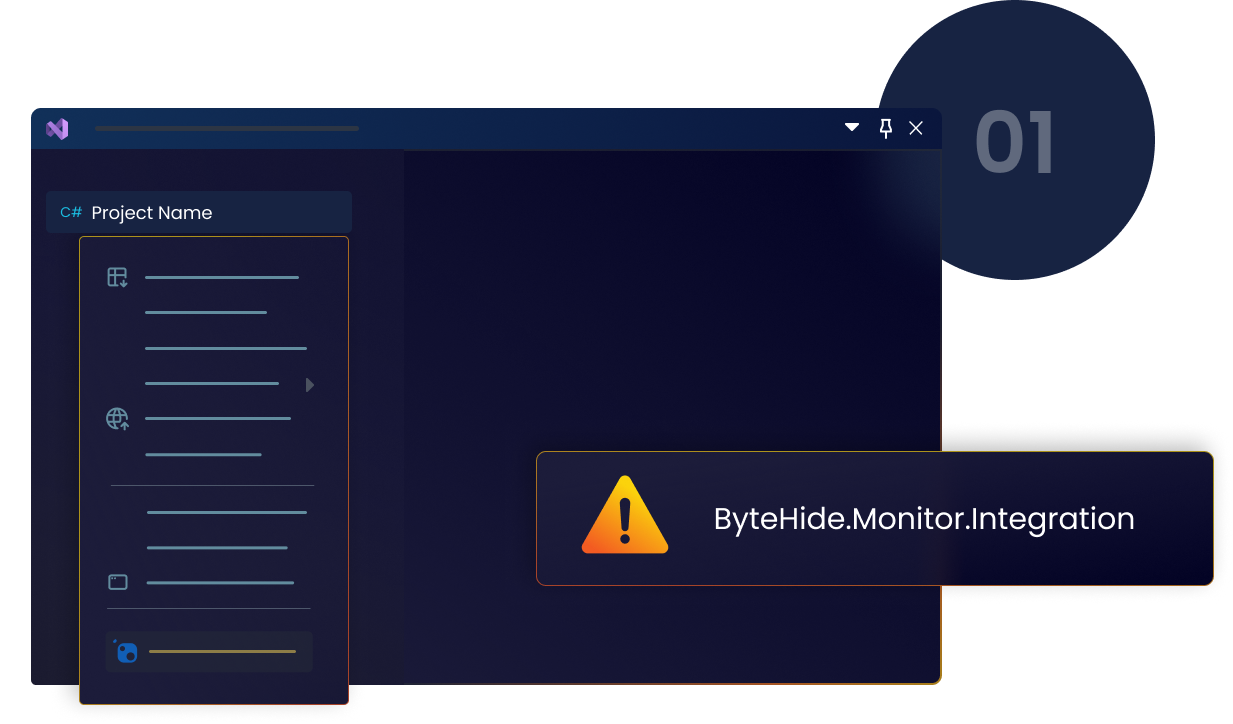
Integrate Monitor
Install a nuget package to inject monitor agent during compilation.
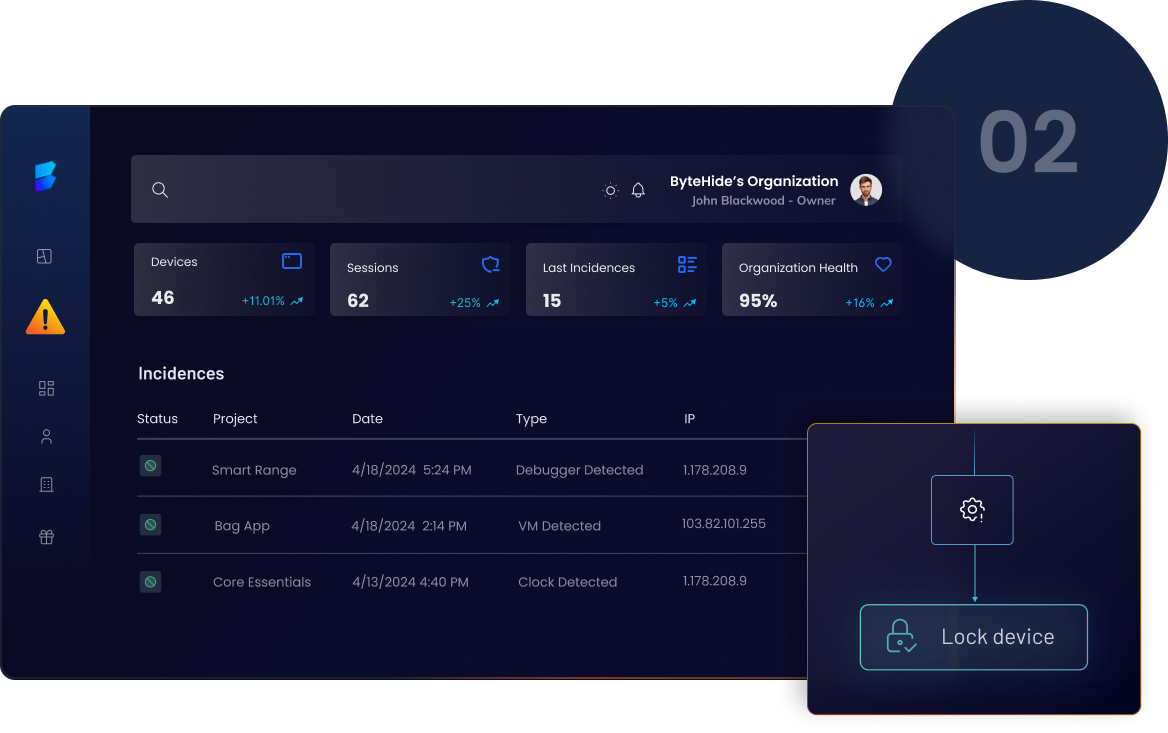
Configure detections and actions
Select what monitor should check and what actions must take.
Deploy and Monitor
Monitor will track your deployed app, detect all security incidents.
Key Players benefits
Using a RASP for Your Applications Security
Developers
Monitor automates the integration of security controls, reducing errors and manual effort. It continuously monitors and responds to vulnerabilities and active attacks, allowing developers to focus on building apps.
Company
Monitor defends against a range of attacks, such as code injection, malware injection and reverse engineering, significantly reducing the risk of data leakage and compromised applications, ensuring business continuity.
CTO & CISO
Monitor provides seamless real-time protection across all parts of a distributed application. It simplifies security management, allowing the CTO to maintain a robust defense without complex infrastructures.
End Customers
Monitor protects personal and business data, safeguarding customer trust by minimizing security breaches. End customers are shielded from identity theft and financial fraud, ensuring a secure and reliable user experience.


EMPOWER YOUR APP’S DEFENSE
Maximize Security, Minimize Effort
Supply Chain Security
End-to-end protection across your software lifecycle
ByteHide delivers a robust software supply chain security platform that safeguards your applications from the earliest development stages to runtime. Our Monitor seamlessly integrates with other ByteHide solutions, offering proactive security and real-time threat monitoring. This synergy ensures true end-to-end defense for your entire application ecosystem, thereby enhancing overall cybersecurity resilience.
AI-Powered Defense
Smart, adaptive security with AI
Empowered by cutting-edge AI algorithms, Monitor anticipates and adapts to emerging cyber threats, offering dynamic and proactive defenses. As attacks grow more sophisticated, our AI-driven approach minimizes false positives while maximizing security effectiveness, keeping your systems secure against tomorrow’s threats.
Easy & High Integration Level
Effortless setup and deep compatibility
Monitor is designed to integrate quickly and seamlessly into your app, including environments with obfuscation and complex configurations. Enjoy high compatibility without the hassle of complex deployments, making your security setup fast and frictionless.
Developer-First
Built with developers in mind
Monitor streamlines security implementation, empowering developers with tools and features that simplify coding and configuration. Focus on building features while Monitor handles the complex aspects of app security, all with easy-to-use, developer-friendly interfaces.
Frequently asked questions
What is Threat Monitoring?
Threat Monitoring is the continuous process of identifying, evaluating, and responding to cyber threats targeting an organization’s network, applications, and data. Utilizing various tools and methodologies, it helps detect suspicious activities and potential security breaches in real-time, thereby allowing for prompt action to mitigate risks.
This is done to protect your intellectual property, avoid reverse engineering, and safeguard sensitive logic within your software. By using obfuscation techniques, you can make it significantly harder for malicious entities to decompile or tamper with your code.
What is a RunTime Application Self-Protection (RASP)?
RunTime Application Self-Protection (RASP) is a security technology that integrates directly into an application, enabling it to detect and mitigate attacks in real-time. Unlike traditional security measures, RASP is designed to understand the context of an app’s execution and protect it from within by monitoring its behavior and manipulating its runtime environment to block suspicious activities.
Why should I monitor my app after its release?
Monitoring apps post-launch is crucial because new vulnerabilities can emerge, and cyber threats evolve constantly. Continuous monitoring helps identify and address potential security issues before they can be exploited. It ensures that the application remains secure, compliant with regulatory standards, and performs optimally over its entire lifecycle.
How does ByteHide Monitor work?
ByteHide Monitor works by embedding security mechanisms directly into your application’s runtime environment. It continuously monitors the application for suspicious activities and potential threats, providing real-time protection. ByteHide Monitor leverages advanced algorithms and behavioral analysis to instantly detect and block attacks, ensuring the integrity and security of your applications at all times.
How does Monitor differ from traditional security measures?
Traditional security measures, such as firewalls and intrusion detection systems, typically operate at the network level and lack visibility into the application’s internal processes. RASP, on the other hand, integrates with the application itself, allowing it to protect from within. This enables RASP to detect and respond to threats that bypass traditional defenses, offering a more comprehensive security approach.
Is ByteHide Monitor difficult to implement in my app monitoring process?
No, ByteHide Monitor is designed for easy implementation within your application monitoring process. The integration process is straightforward and well-documented, ensuring minimal disruption to your existing workflows. Whether you are working with web, mobile, or enterprise applications, ByteHide Monitor provides comprehensive guidance and support to facilitate seamless deployment and configuration.
Is Monitor compatible with ByteHide Shield and Secrets?
Absolutely, ByteHide Monitor is fully compatible with ByteHide Shield and ByteHide Secrets. These products can work together to provide a robust, multi-layered defense strategy for your applications. ByteHide Shield offers additional protective measures such as code obfuscation and tamper-proofing, while ByteHide Secrets securely manages credentials and sensitive data. Integrating these solutions ensures a comprehensive security posture, covering all aspects of your application’s runtime environment and data protection needs.