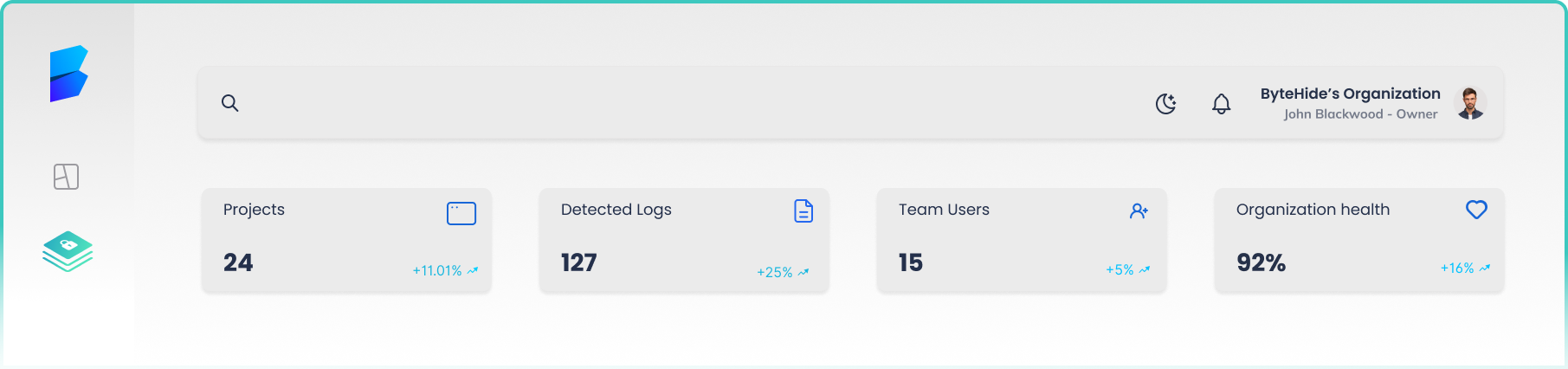
Efficient Log Tracking Software for Better Insights
Process, search and analyze your logs at any scale, No complex query language required.
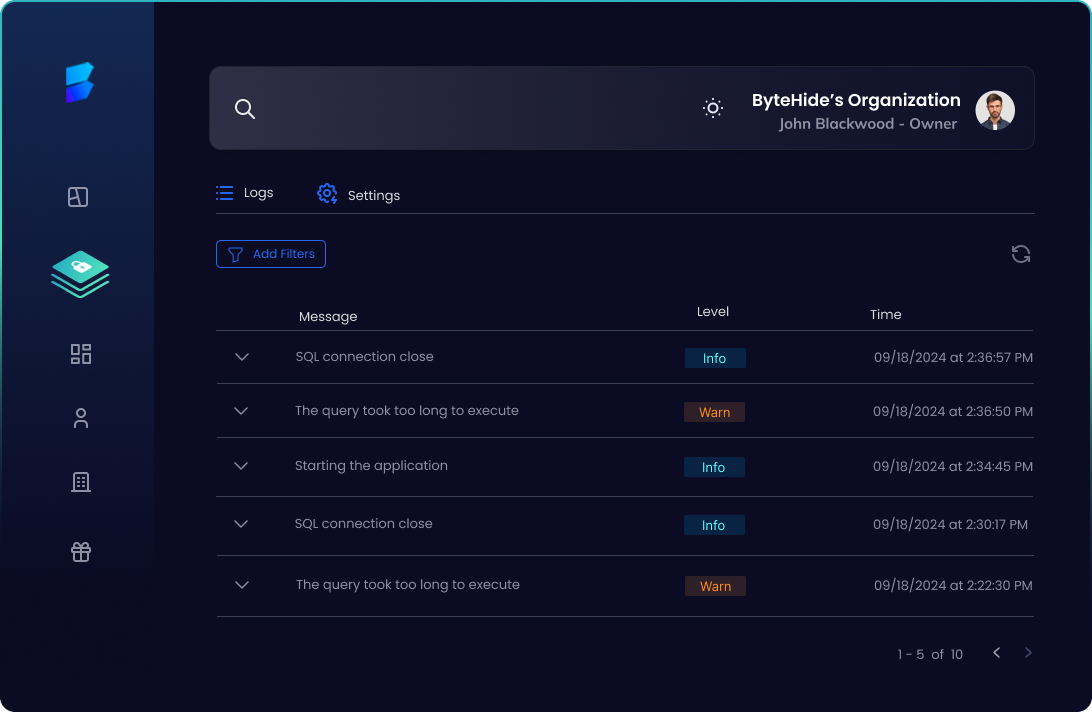
What is a log management software?
A log management software collects, stores, and organizes logs generated by an application, making it easier
to track events, debug issues, and improve performance.
Error
Tracking
Performance
Monitoring
User
Actions
Security
Auditing
System
Events
Error Tracking
Performance Monitoring
User Actions
Security Auditing
System Events
1
Simplify Logging, Maximize Insights
Capture Your Application Logs with Ease
Easily implement advanced logging with just a few lines of code. ByteHide Logs lets you track, structure, and analyze logs effortlessly, ensuring your application is ready to monitor and resolve issues efficiently. Focus on development while we handle the complexity.

Customizable Logging Levels
Define custom logging levels, from trace to error, for precise control over what gets logged and when. Differentiate log entries to simplify debugging and keep your logs organized and clean.
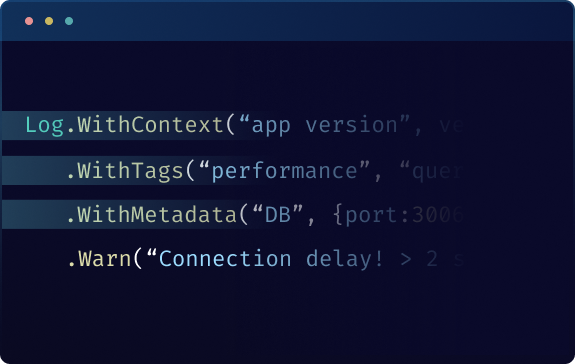
Contextual and Enriched Logs
Add context to your logs for richer insights. Automatically attach metadata such as request IDs, session data, or device info to every log entry, making it easier to trace and resolve issues quickly.
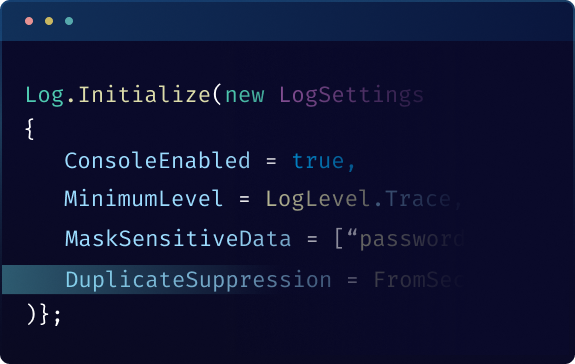
Duplicate Log Suppression
Avoid log clutter by suppressing repetitive entries. ByteHide Logs intelligently identifies and suppresses duplicate log messages, ensuring that only unique and meaningful logs appear.
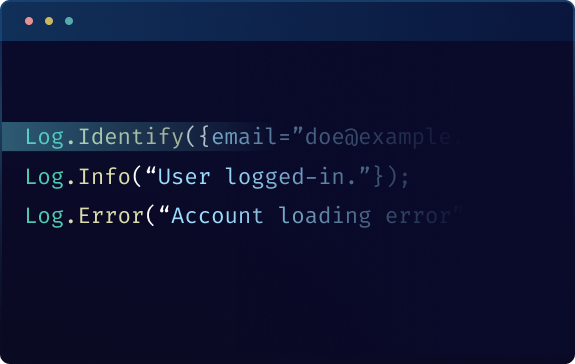
User Identification in Logs
Associate logs with specific users for detailed tracking. Link log entries to user identities, licenses or emails, enabling precise debugging and a clearer understanding of user-specific issues or actions.
2
Built-In Security, Unmatched Insights
Your Logs, Secured and Enriched
Every log entry is protected and optimized for secure storage and actionable insights. From encryption to anomaly detection, your logs remain safe, private, and tailored to your needs, giving you full control while maintaining compliance.
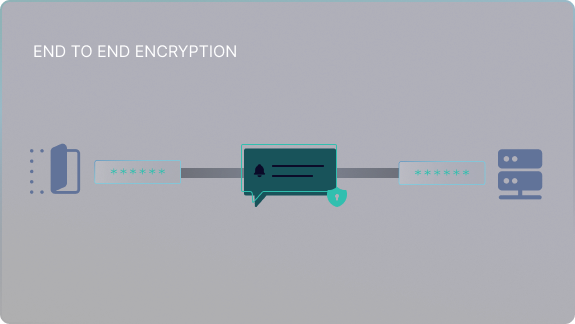
End-to-End Encryption
Protect your logs at every stage. Logs are encrypted as soon as they’re created and remain secure during transmission and storage, ensuring data integrity and privacy.
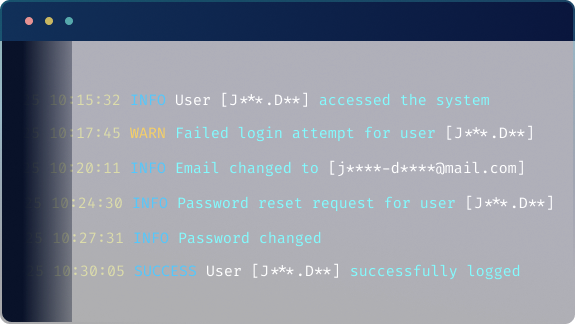
Data Masking for Sensitive Information
Automatically mask personal or sensitive information to ensure privacy and compliance without sacrificing log usability.
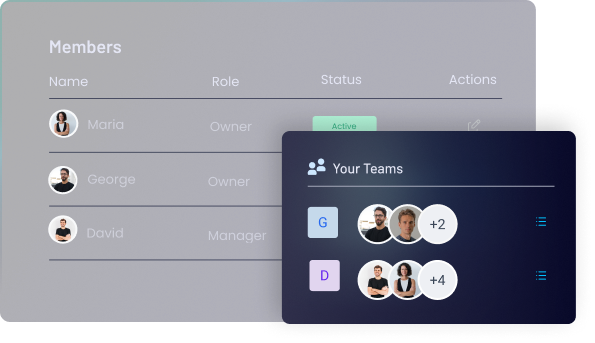
Access Control Management
Assign granular permissions to logs, enabling public, restricted, or temporary access levels to ensure the right people have the right access.
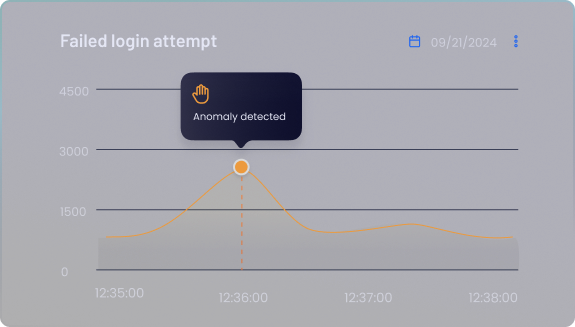
Real-Time Anomaly Detection
Spot irregularities as they happen. Use AI-driven analysis to detect unusual patterns or behaviors in your logs instantly, enabling you to address potential threats before they escalate.
3
Simplify, Centralize, Understand
Effortless Log Management for Developers
ByteHide Logs gives you everything you need to track, filter, and analyze logs efficiently. With real-time monitoring, advanced filtering, and centralized access, you’ll always stay in control of your application’s performance and security, no matter where it’s deployed.
Real-Time Logs
Get immediate visibility into your application’s activity with real-time log updates. Monitor events as they happen to identify and resolve issues instantly.
Exact Log Location
Easily pinpoint the exact location of every log in your codebase with stack trace information. Navigate directly to the line causing an issue to save time and effort.
Advanced Filters
Use powerful filtering options to narrow down logs by tags, message contents, correlation IDs, and more. Combine conditions like “AND” or “OR” for precise searches.
Centralized Log Management
Access all your logs in one place, regardless of where your applications are deployed—on-premise, cloud, or hybrid environments. Stay organized and in control across all systems.
Optimized Visual Interface
Enjoy a user-friendly visual interface designed for developers. Quickly search, manage, and analyze logs with an intuitive design that keeps everything within reach.
Metadata for Deeper Insights
Automatically enrich logs with contextual metadata like user IDs, session details, and request origins. This extra detail makes troubleshooting faster and helps uncover patterns more effectively.
Importance of Logs Management
Risks and problems of not managing logs
in your software
Developers
Without easy and centralized access to logs, developers face obstacles in identifying and fixing application errors. This delays development cycles and can lead to frustration and loss of productivity.
Company
Storing logs locally on devices or servers without proper controls can expose sensitive information, including users’ personal data, which can result in non-compliance with regulations such as GDPR or other data protection laws.
CTO & CISO
The lack of quick and centralized access to logs complicates the response to security incidents or critical failures, increasing resolution time and the impact on the business and comprimising the CTO’s posture.
End Customers
If the logs contain personal or confidential information and are stored on unprotected devices, there is a risk that third parties may access that information, compromising user privacy and reducing user’s confidence in your software
Getting started with Logs
is simple
.NET
.NET installation
dotnet add package Bytehide.Logs --version 1.0.0.0.NET Code
// Startup:
Log.Initialize( new LogSettings
{
Persist = true,
FilePath = "logs/app-logs.txt",
RollingInterval = RollingInterval.Day,
FileSizeLimitBytes = 10 * 1024 * 1024, // 10MB
ConsoleEnabled = true,
MinimumLevel = LogLevel.Trace,
MaskSensitiveData = [ "password", "token" ],
DuplicateSuppressionWindow = TimeSpan.FromSeconds(5),
IncludeCallerInfo = true
});
//Somewhere in your app:
Log.WithTags("performance", "database");
.WithContext("Query", "SELECT * FROM users WHERE id = 1234");
.Warn("Database query delay.");
Log.Identify(new AuthUser{ Id ="12345", Email ="john@example.com" });
Log.Warn("Disk space is running low.");
Getting started with Logs
is simple
.NET
.NET installation
dotnet add package Bytehide.Logs --version 1.0.0.0.NET Code
// Startup:
Log.Initialize( new LogSettings
{
Persist = true,
FilePath = "logs/app-logs.txt",
RollingInterval = RollingInterval.Day,
FileSizeLimitBytes = 10 * 1024 * 1024, // 10MB
ConsoleEnabled = true,
MinimumLevel = LogLevel.Trace,
MaskSensitiveData = [ "password", "token" ],
DuplicateSuppressionWindow = TimeSpan.FromSeconds(5),
IncludeCallerInfo = true
});
//Somewhere in your app:
Log.WithTags("performance", "database");
.WithContext("Query", "SELECT * FROM users WHERE id = 1234");
.Warn("Database query delay.");
Log.Identify(new AuthUser{ Id ="12345", Email ="john@example.com" });
Log.Warn("Disk space is running low.");
COMPARISON WITH OTHER SOLUTIONS
Why ByteHide Logs Stands Out
Traditional Solutions

End-to-End Encryption
Requires additional configuration
Secure Centralized Storage
May require own infrastructure
Simple Integration
Can be complex and time consuming
Masking of Sensitive Data
Not always available
Duplicate Log Suppression
Requires manual configuration
Integration with Security Products
Complex and manual
End-to-End Encryption
Included by default
Secure Centralized Storage
Secure cloud storage
Simple Integration
Easy-to-use SDK, fast integration
Masking of Sensitive Data
Built-in functionality
Duplicate Log Suppression
Automated
Integration with Security Products
Plug & play with the ByteHide suite
Traditional Solutions
End-to-End Encryption
Requires additional configuration
Secure Centralized Storage
May require own infrastructure
Simple Integration
Can be complex and time consuming
Masking of Sensitive Data
Not always available
Duplicate Log Suppression
Requires manual configuration
Integration with Security Products
Complex and manual

End-to-End Encryption
Included by default
Secure Centralized Storage
Secure cloud storage
Simple Integration
Easy-to-use SDK, fast integration
Masking of Sensitive Data
Built-in functionality
Duplicate Log Suppression
Automated
Integration with Security Products
Plug & play with the ByteHide suite
Frequently asked questions
What is ByteHide Logs and how does it improve log management?
ByteHide Logs is an advanced cloud log storage solution that allows applications to securely store and manage their logs. It provides centralized, secure access to encrypted logs, simplifying application monitoring and diagnostics through intuitive search and filtering tools.
How is the security of logs ensured in ByteHide Logs?
ByteHide Logs uses end-to-end encryption to ensure logs are protected from the moment they are generated until they are stored in the cloud. It also implements encrypted communication and secure storage in a cloud infrastructure, ensuring sensitive information is protected from unauthorized access.
What are the advantages of using Customizable Log Levels in ByteHide Logs?
With ByteHide Logs’ Customizable Log Levels, users can define the severity level of logs they want to collect. This allows them to focus on the most relevant information, such as warnings and errors, improving application performance and facilitating more efficient problem resolution.
What benefits does the ByteHide Logs Intuitive Control Panel offer?
The ByteHide Logs Intuitive Control Panel offers a user-friendly interface that allows users to quickly navigate, view, and analyze logs. Its advanced search and filtering capabilities save developers time by facilitating the identification of critical events and optimizing response to application issues.
How does ByteHide Logs assist in diagnosing complex and distributed applications?
ByteHide Logs uses correlation IDs to track requests and processes across different services or components, simplifying diagnostics in complex and distributed applications. This enables quick identification of bottlenecks and problematic areas, accelerating problem resolution.
What security measures does ByteHide Logs implement to protect sensitive data?
ByteHide Logs safeguards sensitive information by automatically masking data such as passwords and tokens in the logs. This feature minimizes the risk of disclosing confidential data, helping comply with security regulations and policies.
How is ByteHide Logs integrated into a .NET application?
Integrating ByteHide Logs into a .NET application is straightforward with its easy-to-use SDK and clear documentation. It supports a wide range of .NET frameworks, including .NET MAUI, Xamarin, Blazor, and ASP.NET, allowing developers to start capturing logs in just a few minutes.
How do ByteHide security products differ from other solutions in the market?
ByteHide security products, such as Logs, offer a comprehensive and adaptable approach that combines secure storage, advanced encryption, and real-time monitoring. This provides robust, centralized protection that adapts to the needs of modern applications, facilitating the management and enhancement of application security and performance.