Protects the software that controls your machines, sensors and embedded devices, even without a constant internet connection.




Why do IndustrialTech companies need App Security?
Modern industrial software runs far beyond traditional data centers it lives inside factories, machinery, vehicles, and edge networks. In these environments, code and secrets are often exposed within firmware or embedded systems, making them vulnerable to tampering or reverse engineering. Remote protection or patching is often impossible, especially in disconnected or air-gapped environments. When critical logic that powers production lines or controls PLCs can be manipulated, the stakes are too high to ignore. And with cybersecurity standards like IEC and ISO tightening, proving you’re protected isn’t optional it’s essential.
ByteHide’s Solution
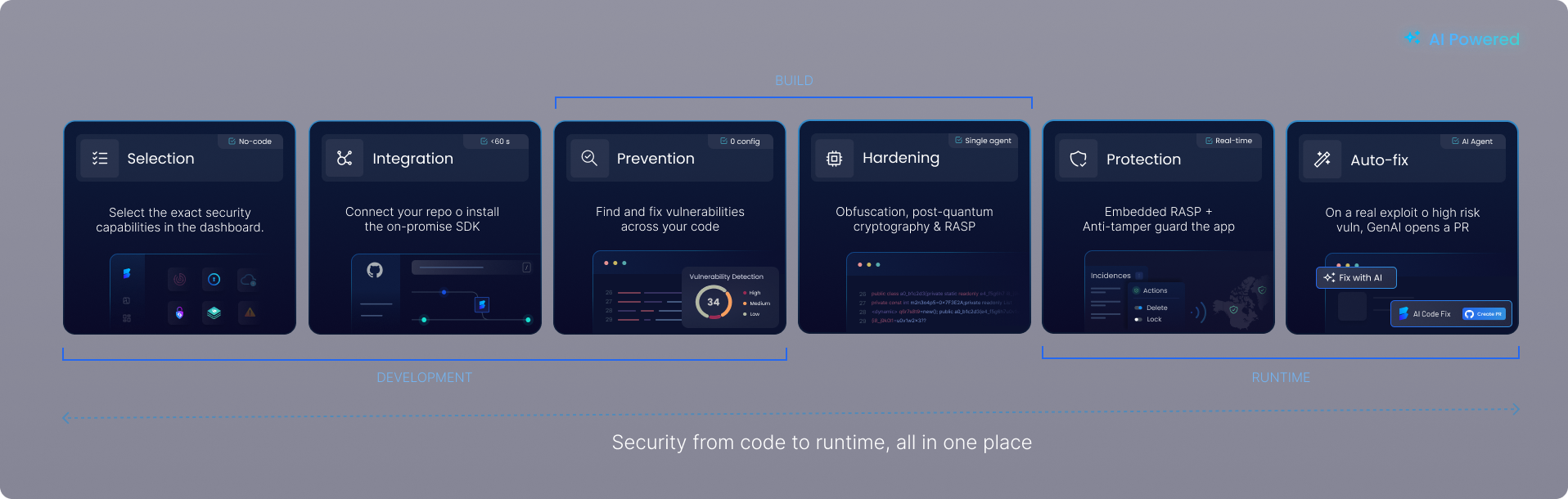
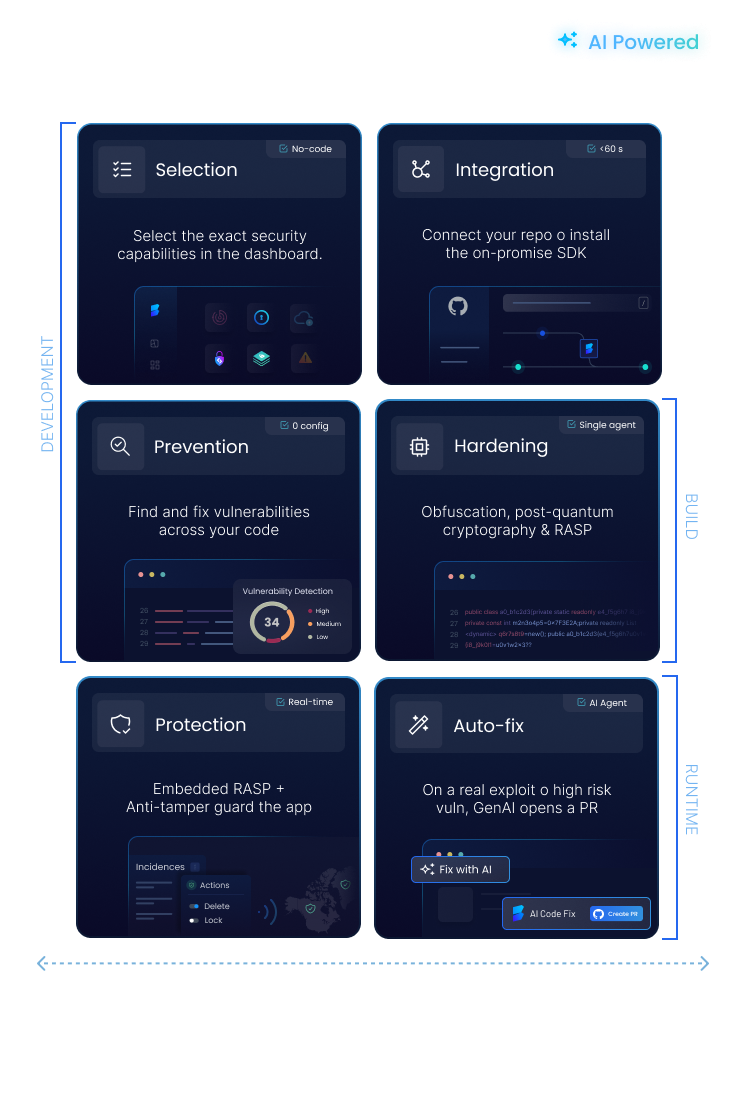
ByteHide unifies your software security within a single platform.
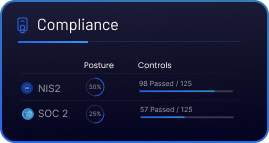
Compliance
Keep Your IndustrialTech Compliance On Track
ByteHide helps industrial software teams comply with critical cybersecurity standards like IEC 62443 and ISO/IEC 27001 by embedding protection into the core of your applications from firmware to edge devices. Even in remote, offline, or legacy environments, ByteHide ensures your systems are traceable, secure, and resilient.
Industrial Automation and Control Systems Security
IEC 62443 defines security requirements for industrial control systems, covering everything from embedded components to entire networks. ByteHide supports this standard by encrypting sensitive data locally, securing firmware logic, and preventing tampering on edge or legacy devices.
ISO/IEC 27001 – Information Security Management
ISO 27001 outlines best practices for protecting information assets in any environment. ByteHide enables compliance by enforcing security from the development phase, ensuring secure configurations, and enabling end-to-end traceability of software execution even when deployed in disconnected or constrained systems.
Next-Gen Security Features
AI Static Code Analysis
Scans your source code for critical security vulnerabilities like SQL injection, XSS, and buffer overflows. AI-powered analysis reduces false positives by 85% and offers AI-driven autofix to remediate issues autonomously. Works out-of-the-box and supports all major languages.

Software Composition Analysis (SCA)
Analyzes third-party components (libraries, frameworks, dependencies) for vulnerabilities. Identifies and manages known CVEs, reducing supply chain risks.
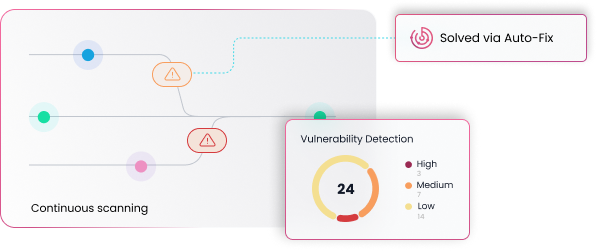
Secrets Detection
Scans your codebase, configurations, and repositories to detect hardcoded credentials, API keys, and sensitive information. Identifies and remediates exposed secrets before they become a threat.
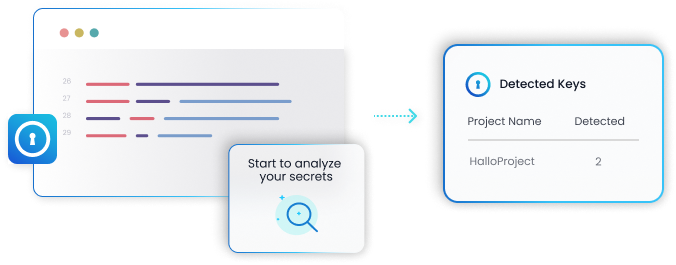
Secure Secrets Management
Provides a centralized, encrypted vault for storing and distributing API keys, database passwords, and other sensitive credentials. Reduces your attack surface and improves security posture.
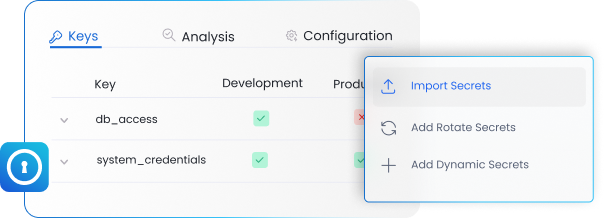
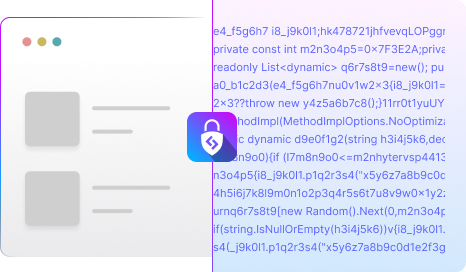
Code Security & Obfuscation
Safeguard your proprietary code and intellectual property from reverse engineering and tampering. Advanced code obfuscation techniques transform your application’s logic, making it extremely difficult for attackers to understand and exploit, while maintaining full functionality.
Runtime Protection & Monitoring (RASP)
Actively monitors and defends your applications against attacks at runtime. Immediately detects and blocks exploits like zero-day threats, injections, tampering, OWASP top 10 and unauthorized access. Ensures continuous application integrity without requiring code changes.

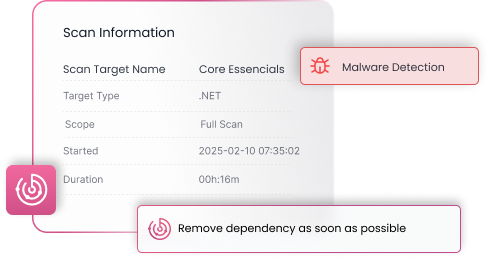
Malware Detection
Protects your software supply chain by detecting malware in dependencies, injected code, and third-party libraries. Proactively scans files and data your application manipulates, including those in storage, to ensure comprehensive protection against malicious threats and maintain system integrity.
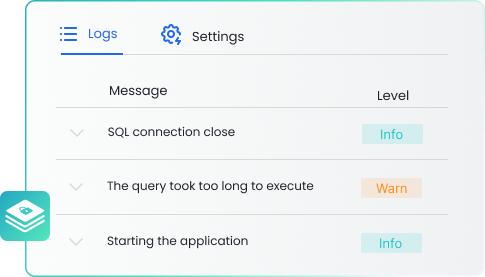
Secure Log Management
Centralizes, encrypts, and manages all your application and system logs. Ensures data integrity, provides irrefutable audit trails, and enables rapid incident response while protecting sensitive information.
Post-Quantum Secure Storage
Protects sensitive data against future cryptographic threats. Offers highly secure data storage leveraging advanced post-quantum encryption algorithms, ensuring confidentiality and integrity even against quantum computing attacks.

Application Security Posture Management (ASPM)
Gain a holistic view of your application security risks across the entire SDLC. ByteHide centralizes security findings from all modules (SAST, SCA, Secrets, Runtime) and contextualizes them to help you prioritize critical vulnerabilities, track remediation progress, and ensure continuous compliance.

Unboring IndustrialTech AppSec for High-Growth Teams
Say goodbye to corporate security headaches. Bytehide streamlines IndustrialTech application security, helping you fast-track code and compliance, while saving valuable time and money.
All-in-one
Secure your software from the first line of code to production. Our comprehensive platform integrates all necessary security tools into one seamless solution.
Up to 7x Faster
Dramatically accelerate fixes. Our AI leverages deep context across your entire security chain, eliminating false positives and autonomously fixing issues where other tools generate noise due to lack of insight.
Up to 65% Cost Savings
Achieve enterprise-grade security for significantly less. Reduce tool sprawl and operational overhead, cutting your AppSec budget while maintaining top-tier protection.
Frequently asked questions
Why is security critical for industrial software controlling machines and remote devices?
Modern industrial software operates in complex environments: factories, machinery, vehicles, and edge networks. This exposes code and secrets within firmware or embedded systems to the risk of tampering and remote attacks, even in disconnected environments. ByteHide offers resilient protection for environments with remote devices and embedded logic, preventing sabotage or manipulation, and ensuring high standards without compromising performance.
How does ByteHide help my industrial software team comply with IEC 62443 and ISO 27001?
ByteHide enables industrial software teams to comply with critical cybersecurity standards. We help with IEC 62443 and ISO/IEC 27001 by embedding protection into the core of your applications, from firmware to edge devices. This ensures your systems are traceable, secure, and resilient, even in remote, offline, or legacy environments.
How does ByteHide prevent remote attacks and sabotage in industrial software?
ByteHide shields your industrial software against tampering and attacks, even in disconnected environments. Through a combination of code protection (Shield), continuous vulnerability verification (Radar), encryption of sensitive data and configurations (Secrets and Storage), and real-time monitoring (Monitor), we mitigate the risk of remote attacks and the sabotage of your embedded logic and devices.
How does ByteHide protect code and embedded logic in industrial environments, even offline?
ByteHide ensures the integrity of your critical industrial software. Our Shield product provides protection for code and embedded logic, even in offline or non-updatable environments. This is essential for safeguarding PLC firmware or the logic controlling production lines against reverse engineering and access to internal keys.
How does ByteHide guarantee the security of sensitive data and configurations embedded in industrial software?
For your industrial software, ByteHide ensures that sensitive data and configurations remain protected. Through our Secrets product, we guarantee the security of internal keys and configurations. Additionally, the encryption of sensitive data and configurations is embedded directly within the software, ensuring their confidentiality.
How does ByteHide offer real-time monitoring to detect anomalies, sabotage, or physical attacks on industrial devices?
ByteHide provides you with critical visibility into the behavior of your industrial software in extreme environments. Our Monitor product enables real-time monitoring to detect anomalous behaviors, sabotage, or physical attacks on devices. This allows you to detect unauthorized reprogramming in PLCs and prevent security incidents.
How does ByteHide ensure traceability and auditing of activity in industrial software, even without constant connection?
ByteHide ensures you always have complete records for audits, even in disconnected environments. Our Logs product offers encrypted local logs that allow traceability and auditing even without constant network access. These logs can then be securely synchronized when connecting to the network.
How does ByteHide address continuous vulnerability verification in industrial software?
ByteHide continuously detects and verifies vulnerabilities in your code and configurations. Our Radar product (AI Static Code Analysis and SCA) is key to this continuous verification of vulnerabilities, configuration errors, and exposed secrets from the first commit, which are critical risk points in industrial software.
What are the key benefits of implementing ByteHide for cybersecurity in IndustrialTech?
With ByteHide, your company gains embedded protection that does not rely on the cloud, compatibility with edge, firmware, and legacy environments, prevention of physical or remote attacks, and industrial compliance without affecting software performance. Our approach ensures high standards without compromising speed or efficiency.
How can ByteHide simplify the protection of your industrial software and guarantee high standards in challenging environments?
ByteHide delivers robust and autonomous security that accompanies industrial software to its most extreme execution, even in environments without constant connectivity. This translates into industrial compliance without overhead and resilient protection against tampering, securing your critical operations without operational complexity.
Fortify Your Industrial Operations
Protect your embedded logic, secure sensitive data in extreme environments, and ensure resilient compliance for your industrial software. Maintain peak performance with autonomous security.

Fortify Your Industrial Operations
Protect your embedded logic, secure sensitive data in extreme environments, and ensure resilient compliance for your industrial software. Maintain peak performance with autonomous security.


