Dangers of Unprotected Avalonia Apps
Leaving your Avalonia app unobfuscated exposes it to numerous threats, compromising its integrity and your hard work.
Discover Vulnerabilities
Unprotected apps are easy targets for hackers who can quickly discover and exploit vulnerabilities, causing serious damage.
Lose Brand Reputation
Security breaches can lead to loss of user trust, tarnishing your brand’s reputation and affecting your bottom line.
Tampering Risks
Without obfuscation, attackers can tamper with your project’s code, modify its behavior, or inject malicious payloads.
IP Theft & Cloning
Unencrypted code makes it easy for competitors to steal your intellectual property and create clones of your project.
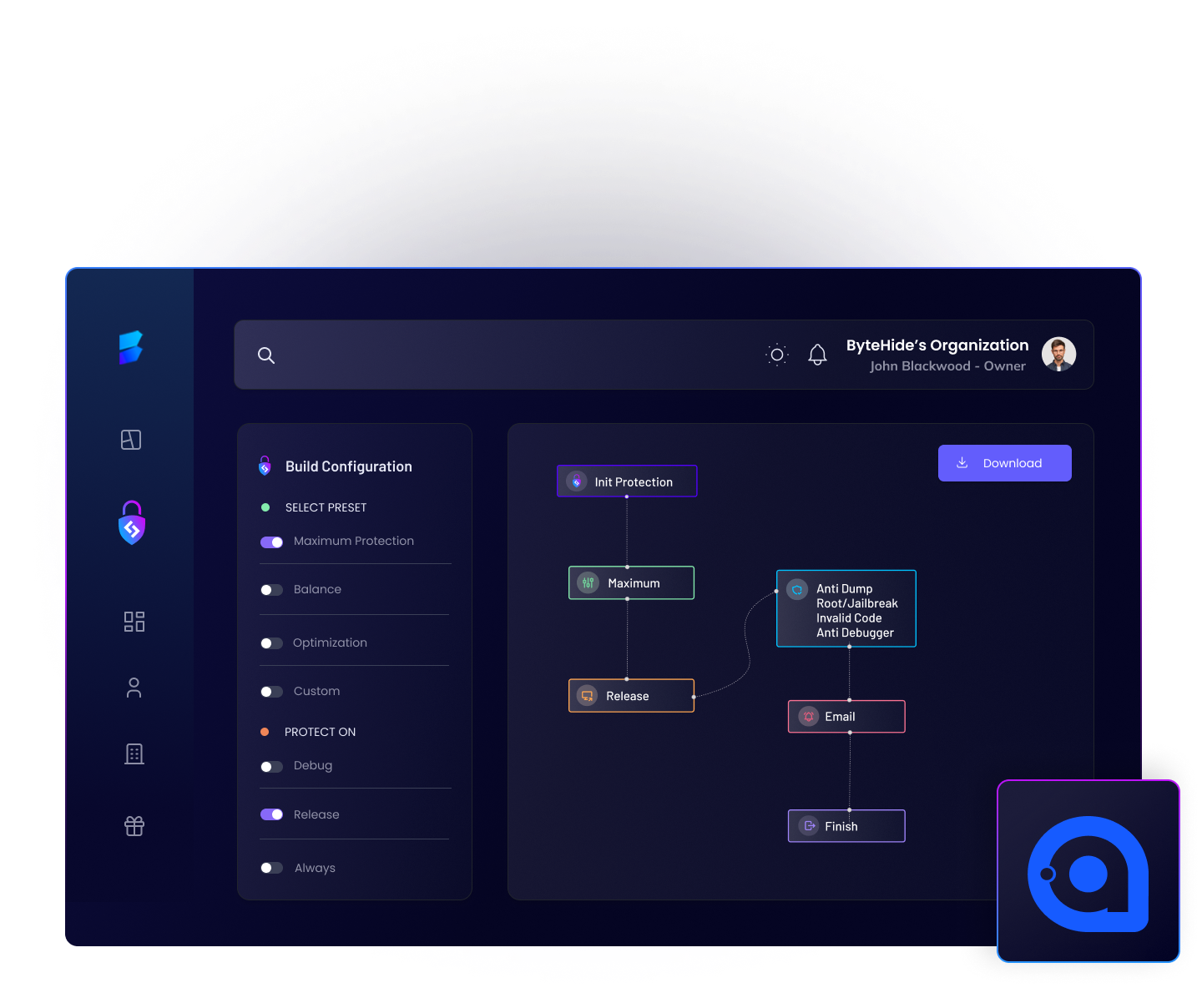
Avalonia No Code Protection in just 2 clicks
Obfuscate Avalonia files with confidence
Shield is an advanced Avalonia obfuscator designed with ease of use in mind. You don’t need to be a cybersecurity expert to protect your project assets and code. Our intuitive interface and powerful features make safeguarding your Avalonia projects a breeze.
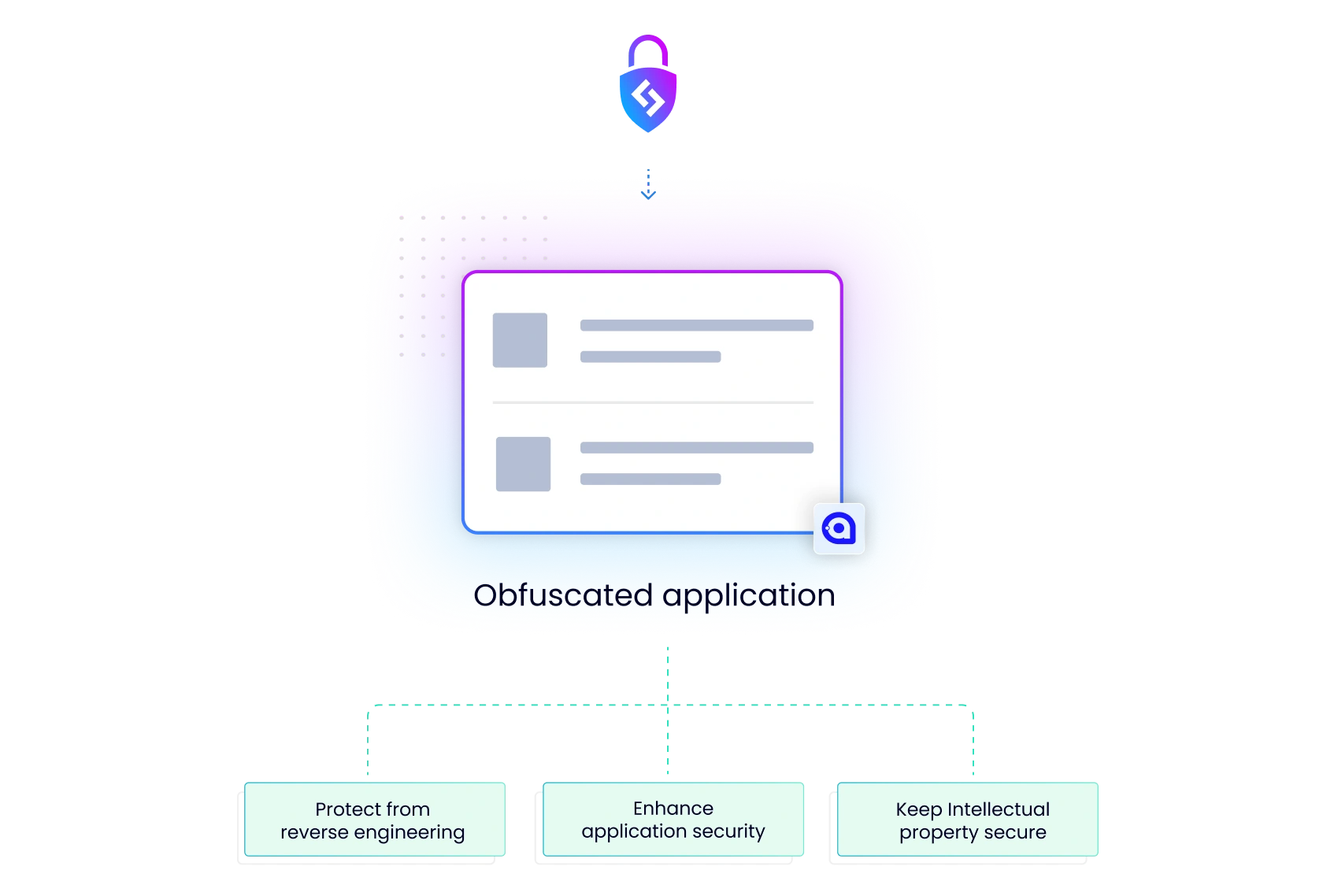

Prevent Decompilation & Reverse Engineering
Protecting your Avalonia files is crucial for maintaining the integrity of your app, preventing cracking or reverse engineering attempts by potential attackers or competitors. Shield ensures that your hard work remains secure, keeping decompilers at bay.
Compliance and regulations
Add robust data protection controls to support compliance with regulations such as PSD2, GDPR, CCPA, PCI and others. Meet compliance requirements with ByteHide Shield.



Support GDPR compliance
The GDPR requires two special articles for the protection of mobile applications. Comply with Article 25: Data protection by design and by default and Article 32: Security of processing by using Shield in your applications.

PCI developer guidelines
There are different requirements listed in the PCI regulations for accepting payments in mobile applications. Shield helps you cover several of these regulations.
Shielding to support PSD2
For mobile banking applications, the security requirements set out in DSP2 point to the need for protection against known and unknown attacks against mobile applications. Shield covers the regulations for your company.
Join +100.000 developers community
ByteHide is backed by a cybersecurity community, many developers and companies use our products in their applications and contribute to open source projects that help the community.
”We had a hard time protecting our application against reverse engineering and integrating it in the deploy phase, with ByteHide Shield we have been able to solve that and focus on the development of the business.
GonzaloCDO at Crypto TechFin
”ByteHide helps us control and manage the different layers of security in our applications, makes it easy for us to work with its automations and allows me to manage my team effectively.
Jorge de los SantosCEO at euler.tools
Using ByteHide Shield to obfuscate applications in their compilation
Frequently asked questions about obfuscation and applications protection
What is obfuscation?
The term obfuscation is commonly used in cybersecurity to refer to making something difficult to read or understand. In the programming world, when the source code of an application is obfuscated it means that it is “modified” using renaming techniques and cryptographic algorithms to encrypt and harden. This obfuscation process is done to prevent the application from being reverse engineered and decompiled to avoid a wide variety of attacks.
Why should I obfuscate my applications?
Just as code once programmed becomes an application, that application can be reversed to get the source code of it. If the source code of this application is accessed without protection, shielding or obfuscation, its operation can be analyzed. This opens up many possibilities for attacks, both cracking and reverse engineering.
If an attacker accesses the source code of your application without obfuscation, he can actually completely modify its operation. In addition, it can steal intellectual property (IP) and cause a very bad image for a business or company, not to mention that there may be sensitive data (such as customer data, passwords or unencrypted database connections) that the attacker or competitor can easily access.
How can I obfuscate my applications?
There are actually many ways to obfuscate an application, from encrypting sensitive parts of the code, to replacing classes or variable names, to anti debugging or anti tampering techniques. All this is only useful if the person in charge of performing the obfuscation has advanced knowledge in logarithmic mathematics, encryption and cryptography. If not, anyone with a minimum knowledge in reverse engineering could reverse all the protections and access the source code. In that case the favorite and most powerful option is to use an obfuscator.
What is an obfuscator?
An obfuscator is a tool that analyzes your application, detects sensitive parts and through different obfuscation techniques increases the security of an application. The obfuscator converts the source code into code that is practically impossible to read by a human, but at the same time maintains its functionality at 100%. The recommendation we always make is the ByteHide Shield obfuscator because it offers military-grade encryption with super-simple preconfigurations. Literally anyone could protect their application with ByteHide Shield in 3 clicks!
Ready to get started?
We have a generous free tier available to get you started right away.

